I am going through the WebGoat exercises, to refresh my knowledge of XSS attacks.
Specifically, I am doing the Stage 1 XSS exercise. This exercise has a form that deliberately does not sanitize input. The solution video shows using the JavaScript alert function to put out a message and the session cookie.
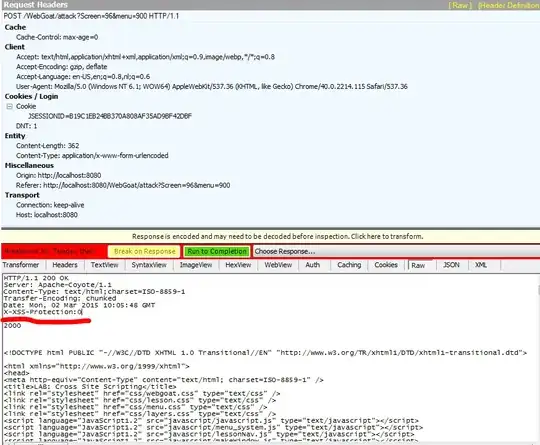
Stage 3 has a built in XSS code snippet, that upon viewing a profile will show the contents of 'document.cookie'.
In any modern browser, all without any add-ons, I cannot get this to execute. I can generate messages using JavaScript alert, but it never prints the contents of document.cookie
The tutorial on this page for get cookies shows that it is possible to print the contents of document.cookie in a JavaScript alert message.
What I would like to know is why I can't do the same in a very simple, deliberately vulnerable to XSS web application. Is there some XSS detection in all modern browsers preventing this? I've tried with he options to disable web security on IE, Firefox and Chrome and it makes no difference.
edit: Things I have tried for both WebGoat 5.4 and WebGoat 6.0.1:
- Accessing via Firefox with a new, default profile and no addons
- Chrome with the --disable-web-security and/or –disable-xss-auditor arguments
- Accessing via Mantra
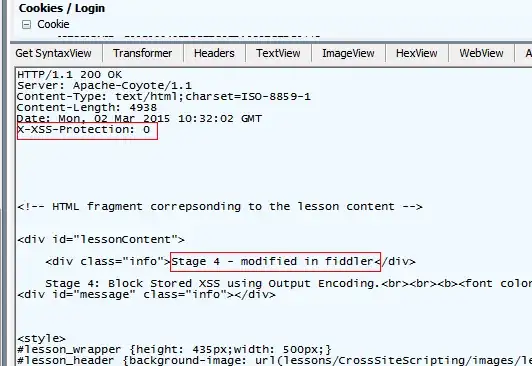
- Setting the X-XSS-Protection header to 0 in my requests.
Is WebGoat trying to teach about an XSS attack that is no longer a threat?
2nd edit:
Per Martin's answer, I tried setting the header manually as seen in the screenshots below. I modified the lesson title so it is obvious fiddler is correctly intercepting the page.
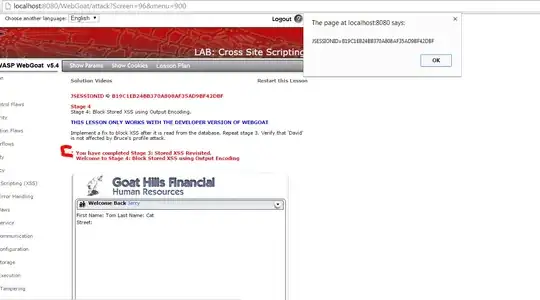
The cookie is not set as secure3 or httponly, but refuses to be read from any browser via JavaScript, via bookmarklet or Scratchpad. The cookie is set correctly in the browser and is viewable in the browsers cookie dialogs.
What property of this cookie is preventing it from being read?