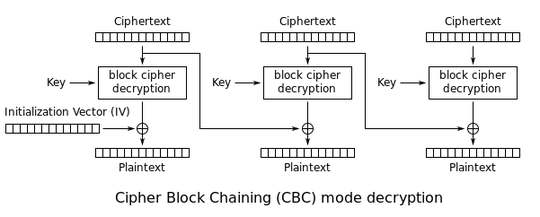
I have a TLS Record containing HTTPs application data.
I extracted the encrypted plain text with mac from the application data, then, when I decrypted the extracted data using AES CBC mode, I am expecting that It will return something like this:
POST /ImeiTracki
ng?msg=010908391
1841060249765020
A984108000001540
F7F9D00DFBF00001
7000160005100000
0000800060200020
7022502080300010
30A0E07918184026
284F8FFFFFFFFFFF
0000000000083083
A758909259672050
B00 HTTP/1.1..HO
ST: h..X-Admin-P
rotocol: globalp
latform-remote-a
dmin/1.0..
....
but instead, it returned:
³Y%þ&É?eĺìr8%
ng?msg=010908391
1841060249765020
A984108000001540
F7F9D00DFBF00001
7000160005100000
0000800060200020
7022502080300010
30A0E07918184026
284F8FFFFFFFFFFF
0000000000083083
A758909259672050
B00 HTTP/1.1..HO
ST: h..X-Admin-P
rotocol: globalp
latform-remote-a
dmin/1.0..
....
The only weird thing here is the first line (³Y%þ&É?eĺìr8%), it should be POST /ImeiTracki. The lines after the first line are all okay.
My input to the aes decryptor:
- encrypted text = encrypted text + mac
- key
- iv
I also tried other https messages from the same session and same result was observed - the first line is unreadable and the latter is okay.
I also tried to use an online aes decryptor and still- same result was observed.
I would like to have a result just like my expectation.
Any ideas on why is the first line unreadable?