My Girlfriend has a years-old laptop from lenovo. I checked it over and wasn't surprised that the Superfish / Komodia Root CA certificate was not present. However I found some others that appear to be similar in function if not purpose.
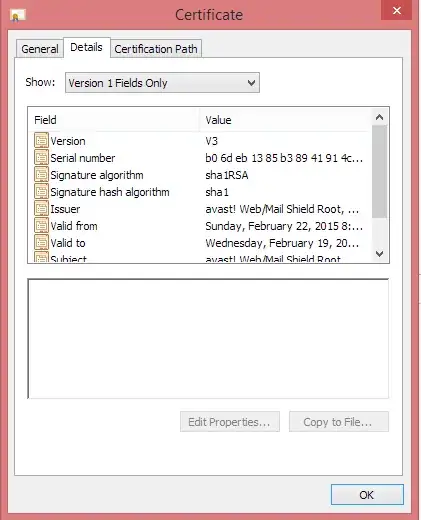
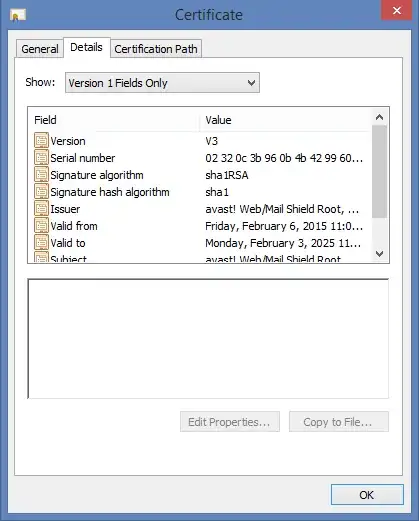
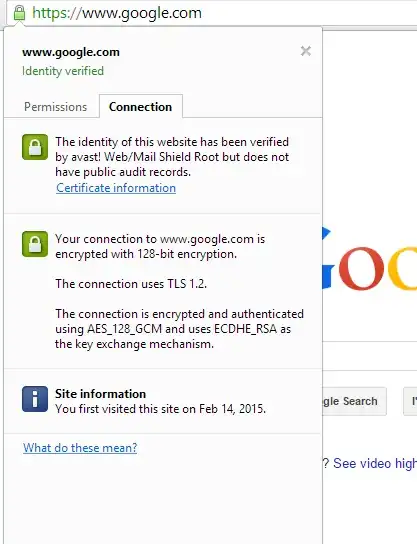
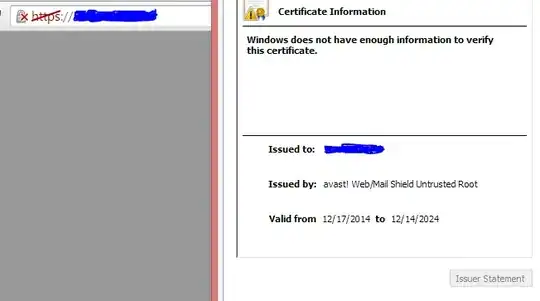
There's keys which appear to have been installed by Avast anti-virus and Skype, both of which are expected to be on the machine. However, the puprose of these keys is presumably quite similar to superfish - interception of secure web content by dynamically creating signed SSL certificates for remote sites.
This potentially opens up similar security issues to what was found with the Superfish software. i.e. if an attacker has these keys they can issue certificates that will be trusted by the local computer.
1). If I understand correctly, in order for these programs to play MITM, they need to have access to the private key associated with the installed cert authority. So it can be obtained by reverse engineering the sotware. Correct?
2) Can anyone confirm whether or not these keys are individually generated for each installation?