I've been working with WPS assessment tools like Reaver and Bully for some time and i could successfully crack my router's PIN code and find its password on both QSS PBC and QSS PIN code. when each of those options was enabled on my router, it appeared in the scan results of WASH command in Linux as a WPS-enabled router that can be cracked.
there are some other routers that when i try to connect to them, it first asks me for PIN code and then the security key but when i scan them using WASH or other such tools, they never show up as a WPS-enabled router. even when i ignore that and try to hack it's WPS pin using reaver or bully, they stick to the first pin even when my signal is 90% strong. the only way that i know that router has PIN is with this method.
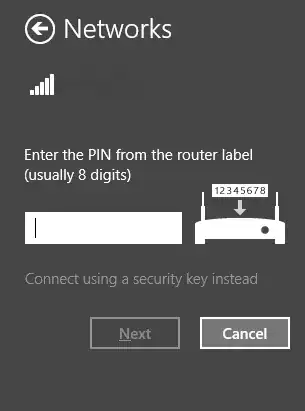
aren't they vulnerable to such attacks? how do they do that?