Question
I have several linux clients connected to an OpenVPN server. Each client is given a persistent IP based on their X509 Common Name. Can I trust these IPs ?
Context
I have Client1 and Client2 connected to Server, all of them in an OpenVPN network:
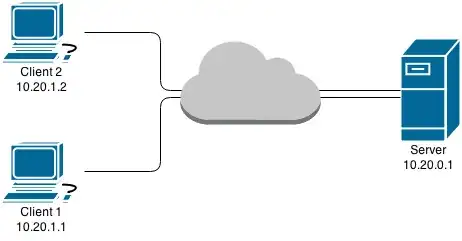
I'd like to set up a NFS share to allow Client1 (exclusively) to access to some files on Server. The TLDP page about NFS and security states that the IP whitelist in /etc/export is "not terribly secure". Does this still hold true inside a VPN ? More precisely, is it possible for an attacker to spoof or take over Client1's IP address in a way that could allow access to the NFS share :
- if he owns a copy of Client2's credentials?
- if he has root access to Client2?
- if he has physical access to Client2?
Specifics
(feel free to assume different software versions, configurations and/or encryption levels if you need to)
- OpenVPN version is
2.2.1 x86_64-linux-gnu The config file at
/etc/openvpn/server.confcontains, among other lines:cipher AES-256-CBC client-config-dir ccdAnd the
ccdfolder contains a file for each client, containing this one line:ifconfig-push 10.20.1.N 10.20.0.1with
Nthe ID of the client (1 or 2 here)ccd-exclusiveis not enabled in the config file- Signature algorithm is SHA1 with RSA encryption
/etc/exportswill allow a single IP to access the share :/some/dir 10.20.1.1(ro,all_squash,sync,subtree_check)
Note: Please point out any other problem with my setup in the comments of the question. I will definitely look into it, but for the sake of leaving an usable artifact let's keep this thread about IP spoofing. Thank you very much for your time!