I have a Debian Linux server which runs a few online game services. I have some competitors in this area and I think one of them is behind the DDoS attacks.
I have full access to the router, so I set a few connection rules in Winbox which can detect and drop the DDoSer IP addresses but I think it's not the best way to prevent an attack.
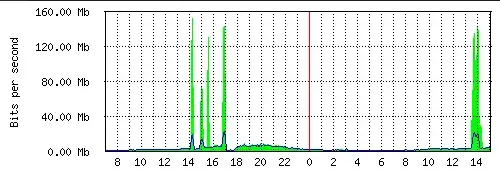
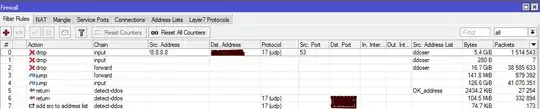
These are some source ip addresses (all from port 53)
- 38.111.134.26
41.78.27.213
66.232.92.39
66.232.92.43
66.243.192.11
67.43.55.110
67.43.55.111
67.50.161.103
67.59.80.28
67.118.192.2
69.27.136.10
69.27.136.12
69.27.211.200
69.31.186.27
74.114.48.151
116.199.220.101
203.87.92.4
203.161.128.249
203.161.159.10
206.51.97.91
206.158.2.91
209.240.96.6
Is there any method to prevent or trace a DDoS attack?