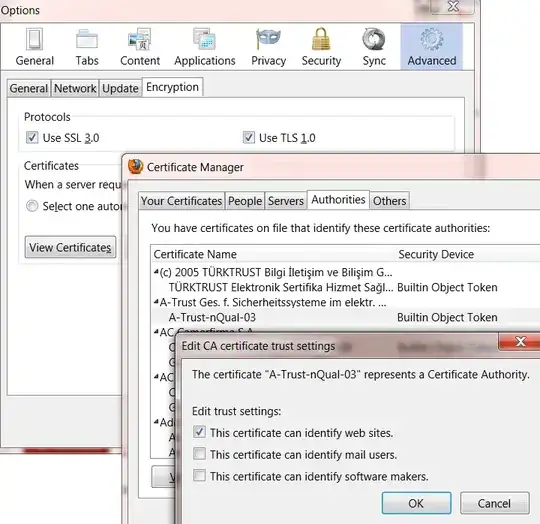
I'm playing around with the idea of running a mini-CA with my (hobby) website, likely only used internally with a few select developers for internal emails, client authentication, staging/development server certs etc. I'm reluctant to extend this style of authentication to my more technically minded users as an optional authentication scheme (despite the benefits), simply because it would require users to fully accept my root certificate and thus I could technically MitM their paypal sessions or something. In their shoes, I certainly wouldn't trust examplehobbysite.com as a valid third-party in the validation of the identity of paypal.com (or any other server for that matter), but I could be happy trusting it for client authentication of users on that site (S/MIME and the like, their CN being their site's username or something).
Simply put, is there any way I could create a root certificate that could only be used to issue X.509 certificates to be used for S/MIME, Client Authentication and the like, and not be valid as Server (SSL) Certificates?