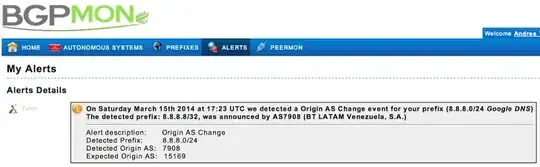
As we know Google DNS server (8.8.8.8) in 14th and 15th March was hijacked in Sao Paulo. And subsequent to this event, BGPmon.org announced an alert.
Now, In a course assignment, we are asked to find AS number of the attacker. I for this question have downloaded related dump files from routeviews.org and found this related messages:
TIME: 03/15/14 17:23:56
TYPE: BGP4MP/MESSAGE/Update
FROM: 187.16.216.20 AS28571
TO: 187.16.216.223 AS6447
ORIGIN: IGP
ASPATH: 28571 1251 20080 7908
NEXT_HOP: 187.16.216.20
ANNOUNCE
8.8.8.8/32
TIME: 03/15/14 17:23:56
TYPE: BGP4MP/MESSAGE/Update
FROM: 187.16.218.21 AS52888
TO: 187.16.216.223 AS6447
ORIGIN: IGP
ASPATH: 52888 1251 20080 7908
NEXT_HOP: 187.16.218.21
ANNOUNCE
8.8.8.8/32
Our TA would say the attacker's AS was 7908 (BT LATAM Venezuela, S.A). But in my opinion it wasn't, because in my view there is no advantages to be exploited by the attacker if he does redirect traffics to his own AS. Despite of this, I couldn't find any update messages originated by this AS in dump files. In other hand, in the picture above, time of attack has been announced 17:23 and from this time onwards, I couldn't find any interesting messages in dump files.
My question is, can anyone please tell me what's the real AS number of attacker?
Thanks in advance