I'm trying to create an open, public WiFi network in my house for guests to use, as I am hosting a (somewhat) large party later tonight. However, none of my routers have any built-in guest networking features, and they do not support alternative firmware like DD-WRT.
Traditionally, what I've done is simply create a double NAT by connecting the WAN port of a second wireless router to a LAN port of my main router. The main router is secured with WPA2, while the second router (for the guest network) is left unsecured. See the diagram below:
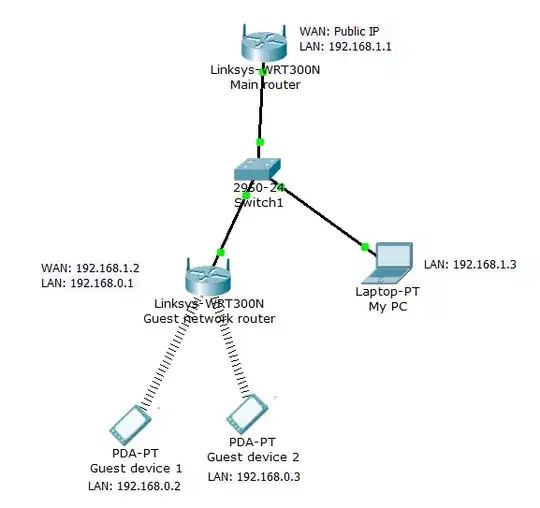
My question though: is this setup actually secure? As in, is there any way for a guest device to access my computer, at 192.168.1.3, or monitor traffic on the main network? I tried pinging while connected to the guest network and it seems like the packets are not reaching computers on the main network, but is there a way to get around this? I read a few articles online about using Double-NAT as a way to create a guest wifi network, but none of them really go into detail about security.
Thanks in advance!
EDIT:
-I drew the diagram in Cisco Packet Tracer because I don't have another program for drawing these diagrams, but I'm not actually using Cisco hardware. The main router is a Verizon Actiontec; the guest network is a cheap Tenda.