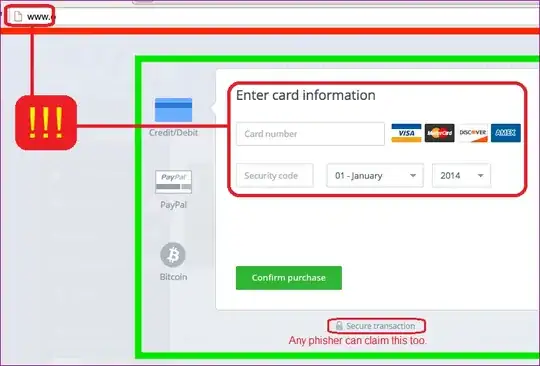
I'd like to protect against clickjacking using the X-Frame-Options header, but we occasionally frame secure content on the insecure version of our site1:
Since it looks like only Firefox currently supports the ALLOW-FROM form of the header, I'm considering conditionally serving the header:
- By default, include X-Frame-Options.
- If your referrer is
^(.*\.)?example.com$, leave the header out.
It seems like this would work, and it fails safe: if someone's browser doesn't send a referrer or a corporate firewall strips it out, they don't get to pay us (which is bad), but our content can never be framed on third-party sites (which would be worse).
How would this strategy work in the real world?
1 Some of our ad partners historically haven't supported serving ads over HTTPS. We're investigating whether this has changed.
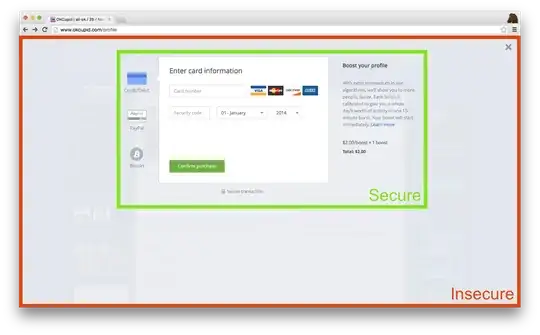
EDIT: To clarify, we only nest a secure iframe in an insecure page in one case: an ad-supported user purchasing something for the first time inline. We can't currently serve the whole site over HTTPS for those users and we don't want to send them to a separate page or open a popup window.
Ad-free users get HTTPS all the time, and we're investigating the feasibility of serving ads over HTTPS too.