I've been looking for ways to improve security and security awareness for both internal and external clients and I happened upon the idea of generating a one-time, random "password suggestion" on the registration and password-change screens, similar to the following:
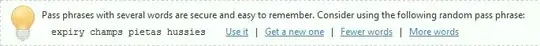
Assuming that:
- The password is generated by indexing all 5-8 letter words in a Scrabble dictionary (about 70,000 words net total) and using a crypto RNG service to choose random indexes;
- The page is viewed over an SSL connection;
- The password is a nonce, i.e. the server doesn't actually save it anywhere;
- Users are not actually assigned this password - they can still create their own, for example if they're sitting at a public terminal.
Is this a good idea or a bad one? I personally like the idea but I'm concerned that my enthusiasm and optimism as a developer might be overshadowing some unintended negative side-effects of a scheme like this.
Should I go ahead with this? Are there ways that it could be improved and/or other things I need to look out for?