From Hackers break SSL encryption used by millions of sites:
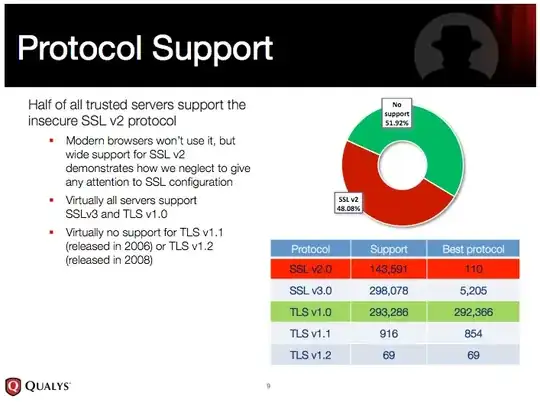
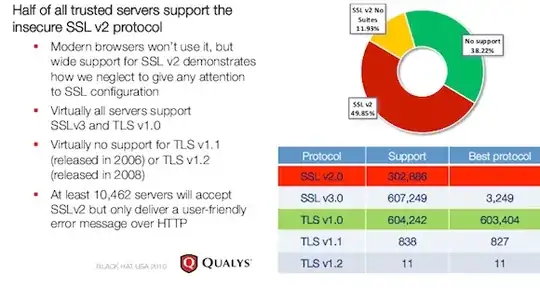
The vulnerability resides in versions 1.0 and earlier of TLS, or transport layer security, the successor to the secure sockets layer technology that serves as the internet's foundation of trust. Although versions 1.1 and 1.2 of TLS aren't susceptible, they remain almost entirely unsupported in browsers and websites alike
Is this true? Are there any statistics that can confirm that many sites/webbrowsers are still using TLS 1.0?