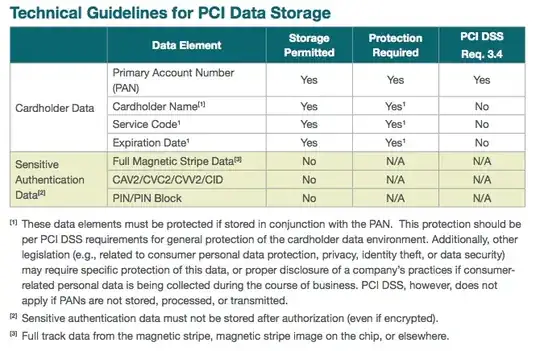
From personal, job-related experience I know that many "Booking Engines" store the CVV info for customers' credit cards from the time a reservation is made until the time the guest leaves the hotel. For people who reserve their rooms a year in advance, that means their CVV data is in the Booking Engine for a complete year!
I'm aware of this because my duties require me to regularly interface with several providers of this service, and this allows me to have access to a multitude of customers' CVC/CVV/CVV2 codes. I have personally observed the applications' behavior of collecting the code at reservation time and retaining it until check-out.
Certain Booking Engines do limit the number of times you can look at the credit card information (I believe one in particular limited me to 5), but the information is still being passed to the Channel Manager and PMS - and I work with all three.
Of course there are certain Payment Gateways which do not require the CVV code to process a transaction. However, many of the hoteliers I work with have Payment Gateways which do.
I'm concerned that retention of this data for such a long period is against PCI-DSS standards, or other legal requirements or industry best practices. I've read answers to one question here on the topic (link below) but the issue is still a bit unclear to me with regards to how this applies for services like Booking Engines.