I was curious how a DoS attack would affect a home router. In particular, I'm interested in how a SYN flood would affect a home router.
The reason I'm interested is due to a Cisco document I read. Within the document, it said SYN flood attacks can affect home routers. To me this seems odd because SYN floods must specify the TCP port to attack.
To illustrate a basic SYN flood against a router, I quickly threw together the following image:
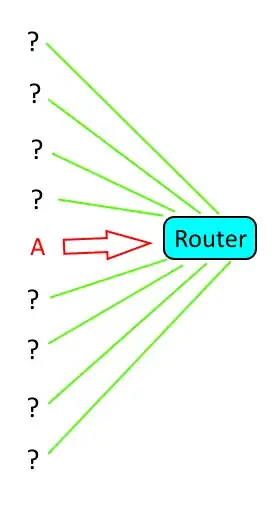
Notes about the image: In the image, the attacker is represented by the red A. The attacker is sending SYN messages to the router. The SYN packets have forged IP addresses to mask their origin. The question marks simply denote the random IP addresses which the attacker has set as the fake origin IP addresses. The green lines reflect the router sending SYN-ACK packets to those random IP addresses.
When executing a SYN flood attack, one specifies the port which they will be attacking as well. As far as I know, a router constantly has different ports open which allows it to be asynchronous. So, how would an attacker know which ports to attack? Wouldn't the attacker need to know which ports are open and when?
The only way I can see a SYN flood working against a router would be if the router had a public port constantly open and the SYN flood forced the router to use up all of its RAM.
Can anybody supply some clarification on this matter?