I am trying to exploit simple stack overflow vulnerability. I have a basic code in c:
#include <cstring>
int main( int argc, char** argv )
{
char buffer[500];
strcpy(buffer, argv[1]);
return 0;
}
compiled using -fno-stack-protector. I've already figured out the buffer length and I've successfully overwritten the EBP and EIP registers. I injected a large number of NOPs, followed with this shell code and finally inserted an address where the injected NOPs are so the code is executed.
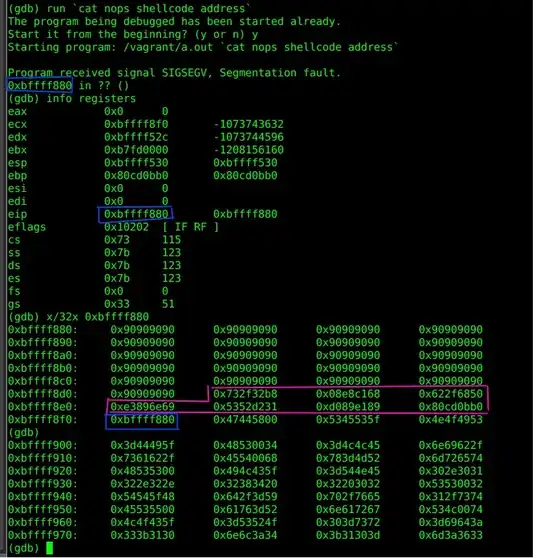
Now the problem. On the picture attached you can see the gdb output. If I run my program with malicious input it gets a SIGSEGV. Dumping the address 0xbffff880 you can see there is a lot of NOPs followed with the shell code (pink box) and finally with the address (blue box).
I've thought this would work as follows: At first the 0x90909090s and the shellcode are considered as simple data. After these (past the pink box) there is an address 0xbffff880. I am saying to the cpu "hey there, now please execute what's on 0xbffff880". The cpu takes what's on the address and executes all the NOPs and the shellcode itself. However that's not happening and SIGSEGV occures.
Where am I mistaken?
I am trying to achieve this on Virtualbox instance of 32-bit Ubuntu 14.04 Linux 3.13.0-39-generic i686 with ASLR turned off.
