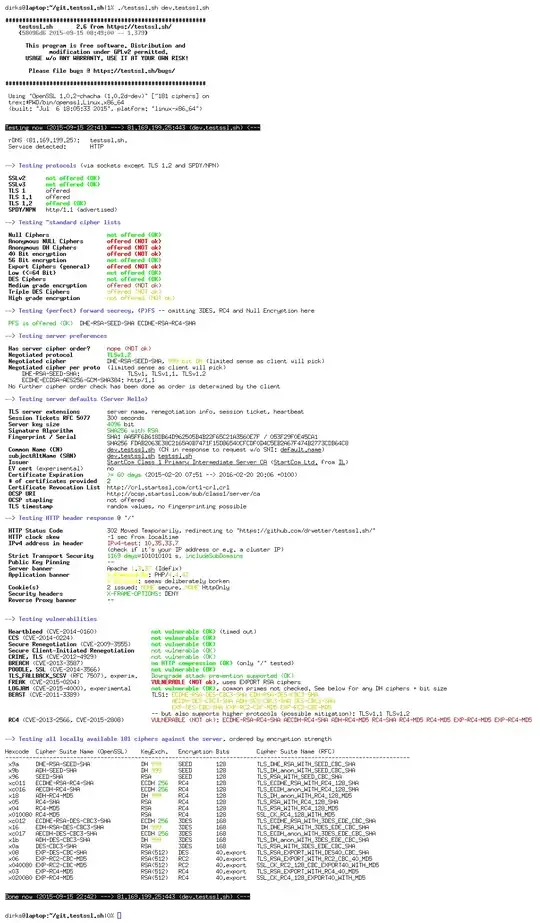
I'm trying to disable SSLv3 in ejabberd 2.1.10 on Ubuntu 12.04. There is no way to disable it in config file, so I have to patch the source and rebuild the package: https://github.com/processone/ejabberd/issues/113
The problem is after patching and installed, how can I verify that SSLv3 protocol is disabled? It is a private server, so I can't use https://xmpp.net/.
I know we can use openssl with -ssl3 option, something like this:
openssl s_client -connect chat.local:5222 -starttls xmpp -ssl3
but the thing is: I cannot disable SSLv3 cipher suites: https://github.com/processone/ejabberd/issues/113#issuecomment-29279707:
Please note that while you can disable SSL version 3, you cannot disable "SSLv3 cipher suites" as there is no such thing, all SSLv3 cipher suites are used also by all TLS versions (TLS 1.1/1.2 just adds some new ones).
so the above command still shows the result:
New, TLSv1/SSLv3, Cipher is AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : SSLv3
Cipher : AES256-SHA
Session-ID:
Session-ID-ctx:
Master-Key: D1D474B68F6C4F59ED5E96963F94FAF078A0C5531A7841B1E0E34257925309A96EA2F25F59F65CCD151F05EB75BC935C
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1414072098
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Two questions:
- how can a online ssl checker (https://www.ssllabs.com/ssltest/, https://xmpp.net/, ...) can test if SSLv3 protocol is disabled or not?
- Is there any risk if SSLv3 protocol is disabled, but SSLv3 cipher suites enabled for some reasons (for e.g OpenSSL on Ubuntu 12.04 disabled TLSv1.2, we have to enable SSLv3 cipher suites to make some monitoring tool worked)?