Boot Process
Secure Boot
There are quite a few steps to booting Windows 8. Now secure boot in general means that the boot loader is only run if its integrity can be checked. In this case, if enabled, the UEFI is started before anything else and checks that the boot loader is signed by a trusted Certificate Authority. For an operating system generally only the manufacturer is trusted, e.g. Microsoft. As long as the boot loader is signed by Microsoft, and verified by the UEFI then the boot loader is started. Even the UEFI drivers are verified[1].
The EUFI contains a database of registered trusted authorities. Users can add their own trusted authorities to this database in order to enable the loading of non-Microsoft operating systems.
This is where Trusted Platform Modules (TPMs) are used. TPMs can be used to store keys, or perform encryption/signing/verification routines. The TPM combined with the UEFI is what allows for the verification of the boot loader, and the loading of an operating system.
Trusted Boot
Now that's not the end of a secure boot process. Now that the OS is in a trusted boot state it begins loading the kernel, system drivers, etc. Secure boot also ensures that the system drivers are signed by a trusted certificate authority (e.g. Microsoft).
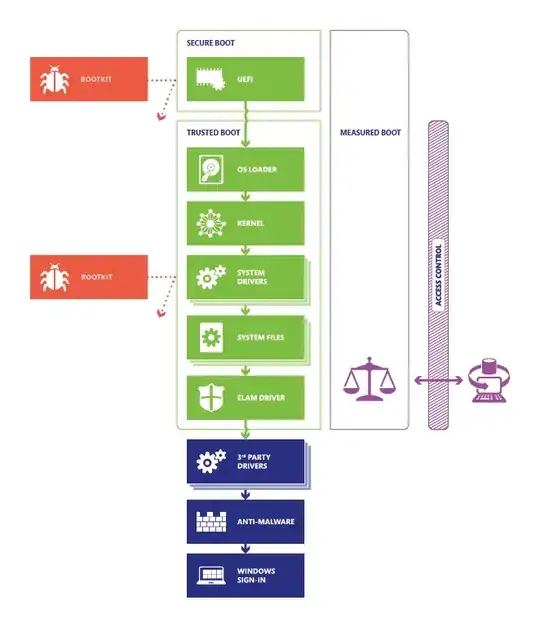
Full description of the image above
Why?
Rootkits
At each stage of the boot process certain pieces of code (drivers, system services, etc) are being registered with the operating system. The earlier in the boot process that malware can hook in the more likely they can:
- Persist: even on reboot, the malware is re-enabled
- Hide: put itself in a position to stealthily keep the operating system (and antivirus) from noticing its there.
- Privileged: continue to grant high permissions to itself
All of these boot processes are run at the highest privilege. Without a secure mechanism for trusting these loaders rootkits could install themselves with high privileges, and the system wouldn't even know they were there. Requiring signed boot loaders and system services/drivers decreases the chances that a rootkit can get a foothold into your system. This does not mean that it's 100% secure, it just makes it a lot harder at certain stages of booting.
Evil Maid
Evil Maid is based on the premise that a hacked boot loader can be installed on the system to do mischief, keylog the password used to decrypt the volume, etc. This is exactly the type of attack this process is meant to prevent. A boot loader could not be flashed on here and successfully booted unless it was signed by Microsoft (or some other trusted authority IF the user decides to trust someone else). This seems fairly unlikely, and it would be unsafe to add a trusted 3rd party to the EUFI database.
Could a piece of hardware come with other trusted authorities installed from the distributor? Maybe, but that's a whole other level of paranoia. If you're worried at that level then you're probably doing something wrong in life.
Enabling User Authentication
The guide above can guide you through enabling a TPM on Windows 8, and setting a password for it. I'm unsure if this also applies to tablets.
