It really depends on the level of precision used by the biometric authentication system. Too precise, and it will trigger false rejections; too lax, and it allows other people to log in as you.
The basic method to authenticate a fingerprint uses pattern recognition, example:

followed by defining the centre of the main pattern, and tracking the relative positions of major minutia features such as bifurcations, ridge endings and ridge islands:
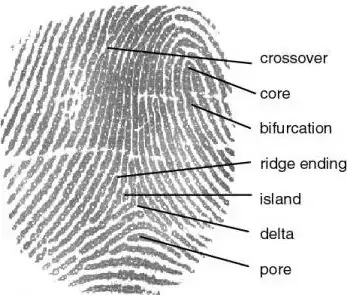
A simple example using a low precision 10x10 grid with centre as 5,5 would generate a password-like encoding such as:
LB23E75 (loop pattern; bifurcation at 2,3; ridge ending at 7,5)
A complex system would use a high precision grid and extract minor minutia features as well as the major ones, resulting in a longer password-like encoding such as:
LD2988B2336E7251X3011 (loop pattern; delta at 29,88; ridge bifurcation at 23,36; ridge ending at 72,51; crossover at 30,11)
These data points are then salted, hashed and stored in the database.
As each fingerprint authentication system is unique, the same fingerprint can produce different encodings. A high precision encoding is very much the same as a very long password. The longer a password, the harder it is to brute-force. Have you tried brute-forcing a 12-character password hashed with MD5?
Being able to crack the hash of a low precision authentication system and reverse engineer a low quality fingerprint does not gain you access to a higher precision authentication system. In any case, you still have to pass authentication (i.e. produce a "real" fingerprint) even if you are able to extract the hash and crack it.
A much easier way is to lift a fingerprint directly from a person so that all data points can be collected. But then, the success of which also depends on the technology used in the fingerprint sensor together with other forms of authentication in place.
What I haven't mention so far is that some systems (especially the government) do store a scanned image of the fingerprint and authenticate by overlaying and comparing graphically with the captured fingerprint. Such a system, when compromised, can render the entire fingerprint authentication scheme useless.