I'm doing some research on the App of my telephone operator. I started Burp Suite on my Mac in proxy mode, then I opened up the App on my iPhone and started to sniff some traffic.
I pressed the "login" button and this happened:
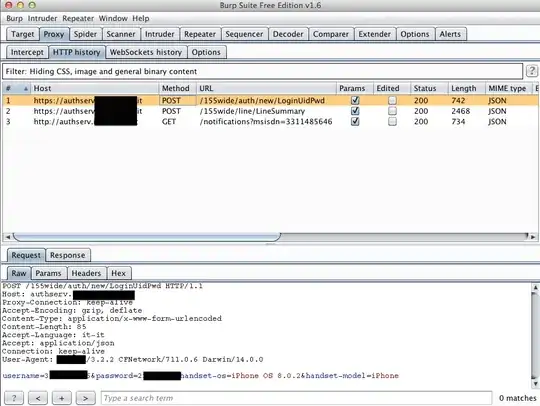
My username and my password are there, in plaintext. The connection is actually HTTPS, but if it's HTTPS, why can I read my username and password as plaintext parameters in the POST request?
Is this normal?
I also tried to replicate the login process with a curl command, and it works only if I use the -k parameter that skip the SSL certificate validation.
What's going on here?