Well, it certainly doesn't make it more insecure. You still have your primary password, which we'll just assume is stored correctly.
And in addition to this (I'm going to assume that you have to enter both, not one or the other; if that would be the case, this wouldn't be very secure, see the links @D.W. provided in the comments.), they have a secondary password. Let's assume it's stored in the worst way possible: plaintext(*).
so we don't care what happens in case an attacker steals the database (hashing of this additional password wouldn't add a lot of security for that anyways).
So my question is, does this kind of secondary password add any security?
This still adds security. The benefit of the randomization is that someone could intercept you logging in once, and still not be able to log in themselves without them taking further steps.
This isn't a whole lot of added security, but it is some and I think it makes sense as an defense in depth strategy.
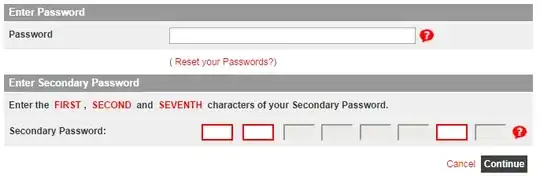
Example of what this might protect against:
You are at a friends house (or you have visitors at your place, or your using your laptop in public for online banking [don't do this]) and have to send them some money. They look over your shoulder and see you entering your password(s). Without the randomization, they can log in themselves and see how much money you have, what you spend it on, etc. And if you forget your cell phone and are using mTAN they can steal from you.
With the randomized second password, they would have to brute force (either the online login or the hash if they managed to break into the bank(*)), or look at you entering the password a whole bunch of times.
There are 8 over 3 = 56 possible combinations of characters to enter (assuming you always have to enter 3 characters), so refreshing until they get asked the exact same characters might be annoying (or might get them blocked).
Maybe they are not quite sure about your primary password and are hoping to just try a couple of variations, which would be a lot more difficult with the randomized secondary password.
So yes, I think there are real-world scenarios which this kind of randomized password protects against, especially against technically less experienced attackers.
(*) Breaking into the bank seems to me like a far less likely attack vector than someone intercepting the password.
Or how much additional security will we have if we use a secondary password without randomizing the letters like this?
You mean just having two "normal" passwords? Assuming it doesn't tell you which password was wrong, it's the same as requiring 16+ characters for a single password for online bruteforce attacks. If they do tell you which one was wrong or if you managed to get the hashes, well then it would add the security an 8 char alphanum password gives you.
This of course doesn't defend against the scenario described above.