Is there a threat from screenshots with blacked out info? That is can someone take out that aftermarket addition so to speak?
For instance
I take a screenshot (using MS snipper)
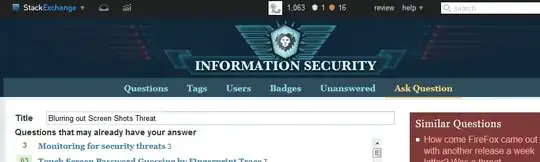
Then I 'blur/blackout' some info
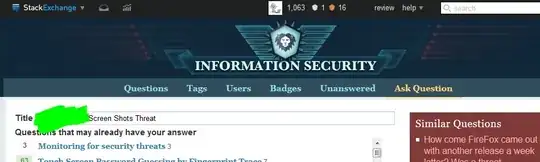
Is the picture above vulnerable to someone looking through its hex values for that extra green layer and just removing it, thus reconstructing the original image (or any other way to 'take off' my attempt of redacting info)?
To make it more secure I always then open up the blurred out screen and then screen capture that.
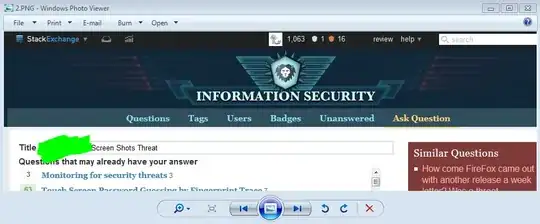
Does the above screen of a screen add better security -there is no way to reconstruct missing data because nothing is "missing"?
I have always been paranoid but after finding out a colleague does the same thing, I'd thought I'd ask.
update So I compared pics one and two (from above) and looked at the hex values, the metadata had not changed at all and the only change was within the image data itself (results below). The results are specific to this particular editor and process. The possibility (likelihood) does exist for data to be recovered if using other tools.