I'm looking for specific examples of things such as:
- Misleading, but common advice
- Advice which has backfired
- Advice which is just, quite simply, incorrect
which have been circulated time and time again, to the detriment of customer security.
I'm looking for specific examples of things such as:
which have been circulated time and time again, to the detriment of customer security.
Banks have been urging the use of debit cards for years, but the policies around reimbursement after a fraudulent transaction are widely variable. It's one thing to have a fraudulent transaction sitting on a credit card statement, but it's quite another to have actual cash missing from your checking account and not be able to pay your rent. I always encourage people to use a good old-fashioned ATM card with no MasterCard/Visa logo; at least that way there's a PIN protecting you.
The notion that the "security picture" during login protects you from an imposter bank has been thoroughly debunked, and is a vestige of the previous FFIEC standards.
Banks tell customers that using security tokens like SecurID or Vasco can prevent malware-based attacks, but the reality is that the malware just sits there on the computer waiting for you to enter an OTP and then sends it to a waiting attacker in realtime. No protection there.
Finally, while login security is important, it's not enough. Most online banking fraud is traceable to malware, and the worst stuff just sits there and waits for you to log in before sending through unrequested transactions. The login can be as secure as you want, but unless you secure the transaction itself, you're still vulnerable.
One last thing - banks are still telling users that their SecurID tokens are completely safe. This is likely incorrect. If the attackers in March made off with all of the seeds, then the tokens are basically worthless. If they made off with only a subset of the seeds, the bank would need to find out for sure if their seeds were stolen. I've yet to hear any bank be able to make a claim on this point one way or another, so I assume any SecurID manufactured before this summer is owned. This doesn't apply to Vasco or anyone else, just to RSA.
Many banks simply do not understand these points, at least outside of their security teams, so the actual advice given out by customer service reps is often wrong on these points. I don't think it's necessarily the banks' faults; you can't expect every customer service rep to be a data security guru, but it does mean that the banks have a responsibility to deliver a secure enough system that bad advice from customer service doesn't matter.
You can have a look at that article from Murdoch and Anderson, on the topic of the "Verified by VISA" and "MasterCard SecureCode" online authentication systems. The article points out several problems in that system, among which the use of iframes which train users into entering personal details on Web pages, the provenance of which they cannot verify.
Advice which is just, quite simply, incorrect
Westpac still clings to their claim that a Java or Javascript point-at-the-screen-and-click picture of a keyboard for entering your (monocase alphanumeric, exactly 6 character) password is more secure than allowing use of the real keyboard. Shoulder surfing is something that only happens to the customers of other banks, it would seem; and visually impaired customers in Australia do not enjoy the protection of the ADA.
Their claim is based on the fallacy that "a keyboard logger can't see what you click on screen", despite a real live phishing campaign explicitly targeting them and their customers over 4 years ago with a Trojan that did precisely that.
There is some hope, though: 12 years ago NAB was making the same claim, but they have since wised up, and now use the same password-entry mechanism that's built in to browsers and used by every sane organisation.
Well of course, there is the advice on password strength. A common thing to hear is insistence on a password with weird symbols. When that insistence is the only thing communicated effectively (like if the important part about length is left out), customers end up making password1 and p@ssw0rd the two most common passwords. Or, it ends in the laughable incident of a password being written on a sticky under the keyboard because it can't be remembered.
Banks, for the most part, are awful about making sure new credit card / debit card users are aware of this simple piece of advice: do not do online banking or use your credit card number at a public wifi hotspot. (For the average customer, this simple rule can drastically better their personal security and awareness.)
Customers need to be told that just because a business uses a machine for credit card transactions they are not necessarily secure. Tell them to be wary of small businesses - not because they're malicious, but because they just aren't in the business of payment security. And, for instance, a small online retailer not well versed in security could just use Paypal or Google Checkout to handle their transactions.
Verification number is used in online transactions to verify owner of the credit card and to prevent frauds. Well, according to banks...
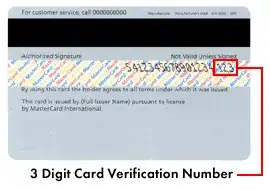
In my opinion, it should be more like a PIN (and it is something like on-line PIN).