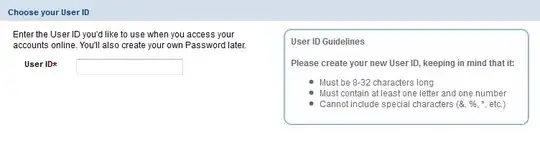
These user names requirement can cause user names to be less predictable. I don't think that this provides a substantial security improvement, but I can think of a couple of scenarios where they help a little. I doubt that it offsets the loss of usability, but I lack concrete evidence to conclude. As usual, security at the expense of usability, comes at the expense of security.: if users are more likely to forget their usernames, this means that either they'll have to store their username in an insecure location (defeating the purpose) or there has to be a way for them to recover their username (which may not be strongly authenticated).
Less-predictable user names improve privacy. If I try to create a johnsmith account and it fails because that username is already in use, this tells me that John Smith is banking with that firm. If John Smith's account is johnsmith1, I need to enumerate more usernames. However, with user-chosen usernames, the suffix 1 is a very good bet. Most websites rely on email addresses as unique tokens — if I want to create an account as john.smith@emailprovider.example.com, I'll need prove that I can read email sent to this address. Banks are usually reluctant to depend on external security, so they tend not to want to depend on email providers.
A significant number of attacks on banking are performed in a home setting — a spouse, a child, a visitor, etc. A less-predictable username can improve confidentiality against a casual attacker who has access to the victim's computer but is more likely to perform opportunistic attacks than to seriously research their attack. Again, with a user-chosen username, the complexity requirement isn't a significant improvement: many users will leave their username pre-filled in their browser, and if they don't choose johnsmith1, the variation is likely to be known to the attacker since they know each other well.
Less-predictable usernames also improve the defense against non-targeted attacks that work by trying out a lot of username+password combinations until a weak one is found. Again, having to try johnsmith1 in addition to johnsmith doesn't provide a significant improvement.
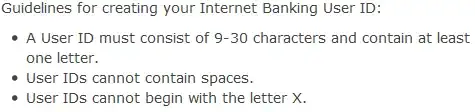
As for user IDs not beginning with X… it's a bank. Deep inside the bowels somewhere is a COBOL program running on an emulated IBM big iron running on a slightly more recent emulated IBM big iron running on an emulated VAX running in a virtual machine on an x86 processor. Before you were born, someone decided it would be a good idea to indicate deleted records by putting an X in the 17th column. The COBOL programmer who was brought out of requirement to fix the Y2K bug offered to fix that as well, but was told that this was outside the job spec and he was not to touch something that works (this could have worked out differently if the bank director's name had been Xavier instead of George).