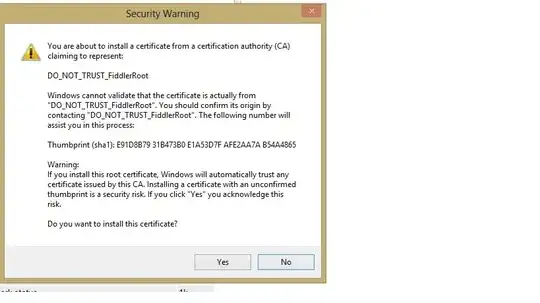
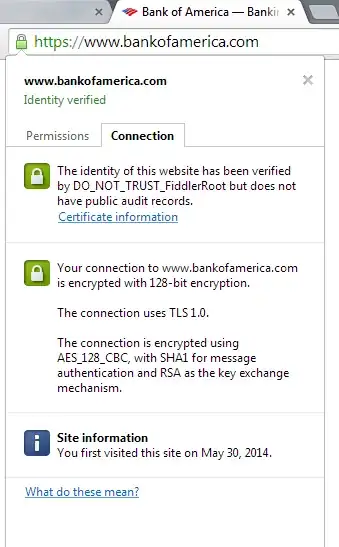
The "DO NOT TRUST" is actually in the certificate itself as created by Fiddler. Fiddler is able to interpret HTTPS connections by acting as an HTTPS proxy. When you connect to a site via HTTPS, Fiddler produces a certificate that claims to be from that site and then accesses the real site. This way Fiddler can see the traffic, but your browser still acts like things are normal.
The problem with trusting it is that the private key for that root certificate is made by the Fiddler executable and isn't particularly well secured. If you trust it as a root certificate, then anyone that gets access to that key can convince your computer that any site they want is a valid site.
A third party certificate is not inherently any more or less secure than any CA cert that comes installed with your browser or OS. All that matters is the security of the private key for that root authority and what policies that root authority has for signing certificates. By trusting a root certificate, you are trusting that everyone with access to the corresponding private key is worth trusting to decide if the website you are accessing is valid.
With a relatively unprotected private key, like Fiddler's, this is never the case, hence Fiddler's warning.