tl;dr - It is incredibly easy to be hacked as an average user. It is also rather easy to protect yourself online. Unfortunately most average users don't see themselves as a target so do not protect themselves appropriately. It doesn't matter if you are not a CEO of a large company, or have very little in your bank account - your PC is a target even if you aren't. Many acquaintances of mine who espouse the virtues of not running antivirus/antimalware etc state that they have never been hacked, but closer analysis shows that all of them have. They just didn't know it or care! Many were part of botnets that could be part of attacks on others. Some just collected account details...
There are various studies posted online which are very scary reading. The online myths page at MIT has these 3 classics (but read the whole page):
Myth 1: The internet is so huge; no one will attack my computer.
Fact: Hackers use automated tools that continually probe computers to find attack vectors. A new, unprotected computer installed on the internet will be generally be compromised within seven minutes.
-
Myth 2: I'll worry about security once someone finally tries to attack me.
Fact: Attacks are ongoing, day and night. Your system must have anti-virus software (to keep out bad/dangerous files) and have up-to-date system software in order to close newly-discovered security holes. Use the bigfix system to keep your system in tip-top shape automatically.
-
Myth 3: Firewalls and anti-virus software will fully protect my computer.
Fact: You must also update your system software for newly discovered security issues. Most of all, though, you must keep your passwords and personal identity information confidential except where they are supposed to be used. Otherwise, your most critical information is at risk. Finally, even frequently upated anti-virus software only protects against known viruses: new malware can sneak by if it hits your computer before the next update.
In terms of how long it takes, this page from SANS is a good starting point:
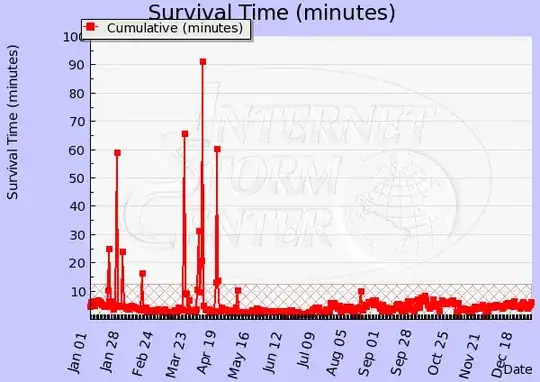
From the page:
The survivaltime is calculated as the average time between reports for an average target IP address. If you are assuming that most of these reports are generated by worms that attempt to propagate, an unpatched system would be infected by such a probe.
