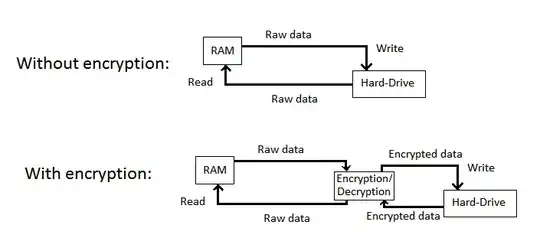
Hard disk encryption is not supposed to alter SSD life time: "encrypted" bits are not harder to read or write than "normal" bits, and (properly done) encryption does not enlarge data. Indeed, the SSD device has no idea whether what it is asked to read or write is encrypted or not. One megabyte is one megabyte.
(Edit: about "encrypting empty space": this implies only one write pass of the whole disk area; this needs not be done regularly, only once. Flash memory can be rewritten about 10000 times before failing, so this extra encryption should not shorten the SSD lifetime by more than 0.01% -- not enough to be detectable.)
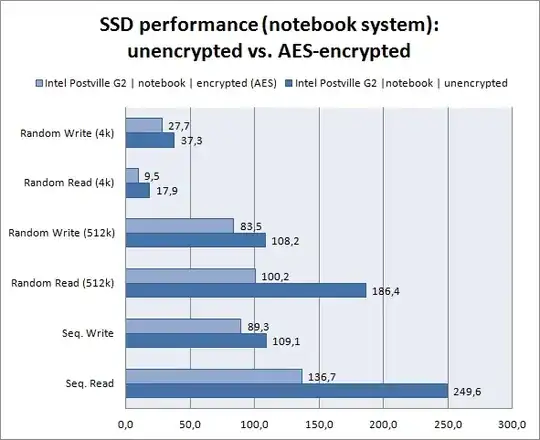
The current state of TrueCrypt being what it is (the "official" software has all but disappeared), it is hard to get definitive answers, and even recommending TrueCrypt can now be a matter of delicacy. Thus, claiming that TrueCrypt will or will not use AES opcodes can be too bold a statement. This article says that, back in 2011, TrueCrypt 7.0a supported AES-NI, and could follow the speed of a SSD (at least the SSD they used for the benchmark).
Performance, in general, is a matter of measurement and should be benchmarked rather than discussed; especially for something as fuzzy as "general computer performance" from the point of view of a human user: the user's feelings are as important as raw figures. The main perceived boost from a SSD comes from the much reduced latency more than from the raw throughput for single-file I/O. We can still speculate that AES-NI allow for more than 1 Gbyte/s raw encryption speed on a 2 GHz CPU; thus, half a core worth of CPU ought to be enough to follow the throughput of a decent SSD (my SSD runs at 500 MB/s and I find it decent enough).
Of course, installing a whole-disk encryption system has the potential, in case of some stupid incompatibility with your OS and/or BIOS booting system, to make your machine unbootable. Make backups ! And prepare a "recovery disk".