I was looking for a form on the US Department of Transportations website, and I came to a page that gave me an error, with a full debug report and stack trace.
Hopefully, you can get the same result by going to the page as well: http://www.dot.gov/airconsumer/air-travel-complaint-comment-form
If not, I've included two screenshots of the page (it wouldn't fit into 1)
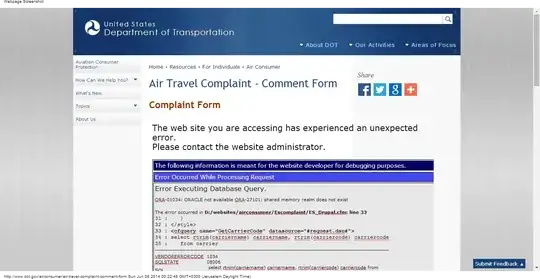
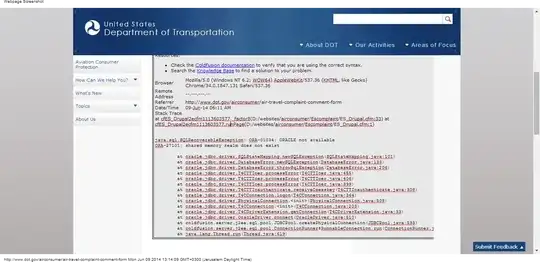
Can this result in a breach of security or is it a non-issue (just an inconvenience and unprofessional page)?
What sensitive information is there on the page and how can it be exploited?
I am asking from a purely academic perspective, and have no intention of trying to enter unlawfully into the DOT's site.