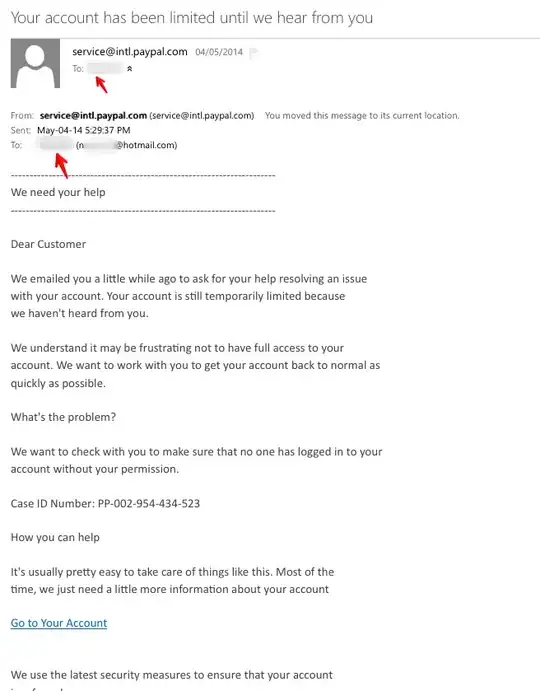
I got this email from service@intl.paypal.com, with the title:
Your account has been limited until we hear from you.
I think this is a scam / spoof email because I don't see any notification in my Paypal account and this is Hotmail account is not used as my Paypal login. (It used to be not any more for more than a year.)
But the troubling thing is, the TO: field has my old password as my name, then my email in brackets. A screenshot below should clarify what I'm saying. I've blurred my email and the two red arrows are pointing to what was my old password in plain text.
Is there anything I could do to protect myself? Does that mean the sender has me under their "contact book" with my name as my password? I have already forwarded the email to spoof@paypal.com.