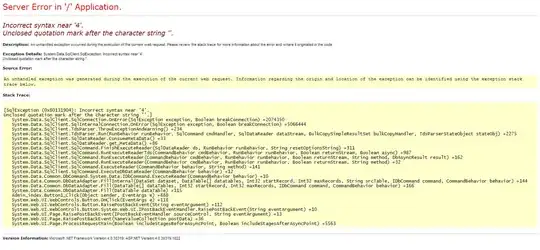
I'm testing a client's web site vulnerability to SQL injection, which appears to be the case. The web site is hosted in IIS on a Windows server and is using Microsoft's .NET framework with SQL. I'm able to enter SQL statements in the sign in form.
But when I enter ' or 1=1;-- in username, it replies "Your Account Has Been Blocked". Obviously, the field isn't validated which is a serious security issue.
How can I obtain the database's content using the SQL injection technique? I've read this penetration test tutorial, but no luck so far.
When I enter ' in the username field, this is what I get: