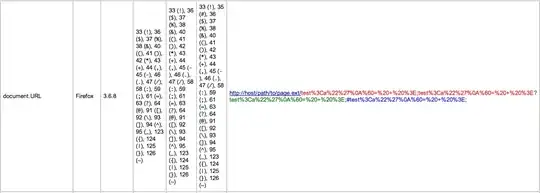
I am trying to perform DOM XSS attack to exploit a vulnerability of localhost webpage. I am able to perform the attack successfully on IE-11 and Chrome. But Firefox is preventing me to perform the attack by encoding the script I put in URL. I am performing the attack as explained on official OWASP page. In order to bypass the XSS auditor of chrome I am following the trick explained in this amazing article (even though he explains Reflected XSS in article but it works well for DOM XSS also). So how can I perform DOM XSS attack on latest Firefox?
Note: I am able to perform Reflected XSS with Firefox (example) but I want DOM XSS specifically where the information is not sent to server.