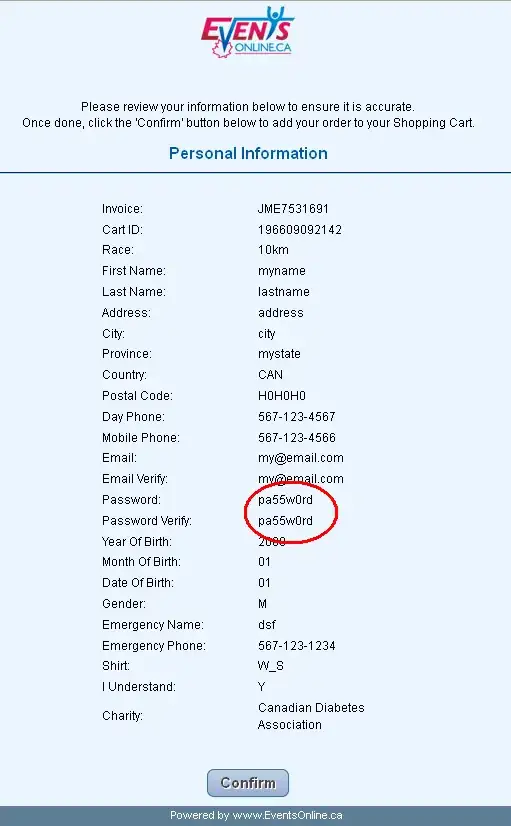
Given the details added in your edit, I would say chances are that your password is not being stored securely.
Your data over the network is safe, given that it is using https. However, it appears that your password is being stored either as plaintext or encrypted (not much better). We could say that maybe they just do this in the short term, but we can use Occam's Razor here. What is more likely? That a developer took the time to use a temporary storage mechanism just to email you your password in plaintext, and then hash it securely? Or is it just stored as plaintext (or some kind of encryption).
Since you mention using the same password for other sites (your mistake), I'd go ahead and change your password for other sites. It probably would be "ok" but you have posted this to a security-centric site, so someone here might get curious about what else is weak. (They would be jerks - this is for charity, but hey, it happens.)
To sum it up:
What is wrong with a confirmation page displaying my password?
Nothing, inherently, except that onlookers can see your password displayed. It indicates a certain level of thoughtlessness when it comes to security. The fact that you also get it emailed to you in plaintext further indicates that your password is being mis-managed. In cases like this, you give up only information you don't mind being compromised, and choose a unique "throwaway" password.