I was trying out a simple stack buffer overflow exploit by creating a malicious crash.m3u file.
as you can see the EIP pointer is overwritten by "A" but EBP hasn't changed. isn't EBP supposed to get overwritten before EIP??
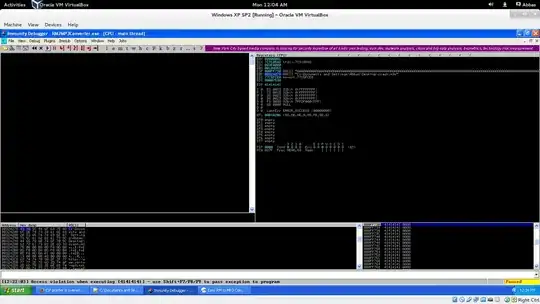
I was trying out a simple stack buffer overflow exploit by creating a malicious crash.m3u file.
as you can see the EIP pointer is overwritten by "A" but EBP hasn't changed. isn't EBP supposed to get overwritten before EIP??

Well, registers are not values in the memory waiting to be overwritten by your buffer!
In the context of a buffer overflow, you do not simply keep writing until you reach some EIP register "location": instead, you replace values on the stack and one of them may end up being the return address of your function. After you've overwritten the stack, the execution resumes as if nothing had happened. The instructions are carried on, and depending on what they are, EBP may or may not be modified.
Finally, provided no exception has occurred in between, you reach the ret of the function. That's when the return value is read from the stack and moved to EIP.
So in your case, if the ret instruction is never reached, there are still some ways to get command execution. The most likely candidate here is through SEH manipulation.
Have fun!