I like to store mine on paper.
Using a JavaScript (read: offline) QR code generator, I create an image of my private key in ASCII armoured form, then print this off. Note alongside it the key ID and store it in a physically secure location.
Here's some that should work for you no matter what operating system you use, as long as you have a browser that supports JavaScript.
For Windows users:
Click here to download the JavaScript QR code generator: https://github.com/davidshimjs/qrcodejs/archive/04f46c6a0708418cb7b96fc563eacae0fbf77674.zip
Extract the files somewhere, then proceed edit index.html per the instructions below.
For MacOS or Unix users:
$ # This specific version is to avoid the risk that if someone hijacks `davidshimjs`'s
$ # repository (or he goes rogue), you will still be using the version that I vetted.
$ # For the truly paranoid you don't trust GitHub either, and you will want to verify the code you download yourself.
$ wget https://github.com/davidshimjs/qrcodejs/archive/04f46c6a0708418cb7b96fc563eacae0fbf77674.zip
$ unzip qrcodejs-04f46c6a0708418cb7b96fc563eacae0fbf77674.zip
$ cd qrcodejs-04f46c6a0708418cb7b96fc563eacae0fbf77674/
$ # We need to edit index.html so that it supports pasting your PGP key
$ # Open the file in a text editor like Notepad, vi, or nano
$ vi index.html
Change line 11 from:
<input id="text" type="text" value="http://jindo.dev.naver.com/collie" style="width:80%" /><br />
to:
<textarea id="text" type="text" value="http://jindo.dev.naver.com/collie" style="width:80%" /></textarea><br />
Now navigate to the directory you get here with Explorer, Finder, or Nautilus, etc.
For example:
$ pwd
/Users/george/Documents/Code/qrcodejs/qrcodejs-04f46c6a0708418cb7b96fc563eacae0fbf77674
$ open .
Now, double click on the index.html file you just edited and saved.
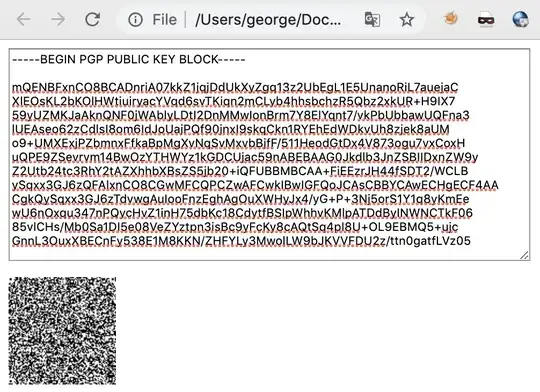
You will most likely need to break up your PGP key into quarters or even smaller to create nice big QR codes that you can easily scan later. After pasting in the text area, click away from the text box and your QR code should appear. Save each one as you go and name them appropriately so that you know their order!
After you've created all the codes, scan them with, for example, a mobile phone QR code scanner app. For the paranoid, keep this device offline once you've installed a barcode reader and then perform a full wipe and factory reset of the device before putting it back online. This will prevent the QR scanner app from leaking your PGP key.
If you have a large key or lots of keys I recommend paperbak, although be sure to write down instructions on how to recover the data later. Just as important as how you back it up is how you restore it from a backup. I'd probably try this with dummy data just to be sure you know exactly how it works.
Worth noting you can protect your private key with a passphrase, so even if it's hosted with a cloud provider they can't see your private key, but then all your password security is reduced to that passphrase rather than the full private key, not to mention cloud providers can disappear overnight.

