I'm working on a tool that exploits SearchIndexer.exe on Windows 7 x86 and connects back to a metasploit multi/handler, using standard metasploit reverse TCP stagers.
The exploit seems to function as intended in the debugger, and works for other processes such as calc.exe.
However, when exploiting SearchIndexer.exe, the TCP connections back to my metasploit instance fails (no traffic sent), and on the victim I can see the following in events in procmon (http://i.stack.imgur.com/Or2L6.png):
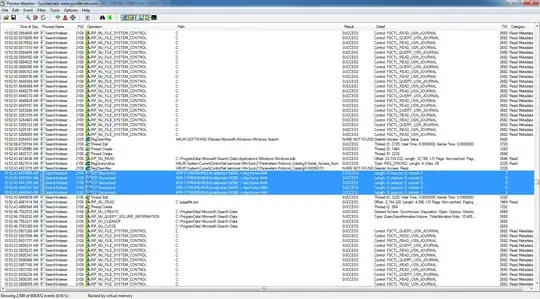
Two questions:
- Are there processes in Windows 7 that are not allowed to make TCP connections?
- If not, how can I debug why the TCP connection (call) fails?