Safe is a big word, and depending on how tempting of a target you are, achieving it in public might not be possible. XKCD #538 - Security that's rather popular here explains this pretty well:
Ideally, if you don't really have to connect to public access points, you wouldn't. But since this often isn't the case, and you still might...
So first order of business should be minimizing your network footprint. You mention in comments that you're using Windows 7. Your operating system will ask you how trusted is the network you are connecting, when you'll be establishing a new connection. It will remember your selection for the next time, so you might want to pay attention when connecting to public Wi-Fi routers next time (if that's the case, select the AP you're connected to in the list, left-click and select "forget"... I think it's something like this IIRC), in case you marked it as more trusted than you ought to. But if you select "Public network", your operating system will automatically disable any unsafe protocols, like e.g. "File and printer sharing for Microsoft Networks", turn on firewall (in case it was turned off before), reset the list of approved firewall exceptions, and do a few other things to prevent any file sharing from happening unwittingly:
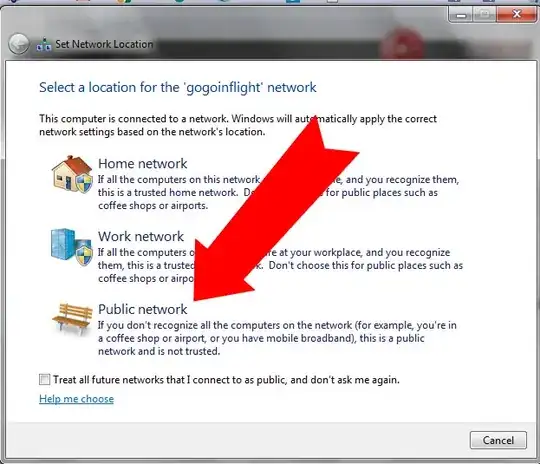
Selecting this option, this connection will only communicate through TCP/IP protocols (IPv4 and IPv6), so assuming no other infection already present on your computer, or later infected through a malicious website, you should stay as safe as the websites you browse and your actions there are. Of course, you shouldn't neglect a chance of a Man-in-The-Middle (MiTM) attack, redirecting your requests to a phishing location, or modifying website responses, so don't ever authenticate with a website using HTTP (non-secure connection), and don't even open them if you expect to be authenticated automatically through a saved web browser user session (cookies), to prevent session hijacking. Ideally, you'd clear your browser cookies (browser history) before opening any previously saved bookmarks or other sites you might be logged in to.
Install HTTPS Everywhere browser extension, only authenticate or send other sensitive information when a secure connection with a website is established via HTTPS, the displayed website location matches the one you expected (mind tiny, hard to spot changes in the address), and the certificate for that website address is valid (browser doesn't report any errors). Usual caution applies, and following these recommendations doesn't guarantee your safety, if you then browse untrusted websites.
But assuming you didn't manually enable networking protocols for your wireless connection, and you're not infected from before, just staying connected to untrusted Access Point (AP) won't put you at risk of unwittingly sharing your files. Something (an infection, user intervention,...) would have to enable any of the required networking protocols for your Wi-Fi connection first, or an infection would have to transmit your local data through enabled ports and using enabled protocols (so TCP/IP only), for that to even be possible.
Oh, and be cautious of shoulder surfing in public places, public AP or not. And that doesn't go merely for people ogling your keyboard as you type passwords, this goes for cameras too, visible or otherwise. Type with one hand and use the other over the fingers of your typing hand, or cover it otherwise. Better yet, don't rely on typing your passwords at all and use multifactor authentication (e.g. combination of biometric readers, typed passwords and smart card stored authentication keys - i.e. something you are, something you know, and something you have), or at least a decent password manager for your authentication needs to avoid typing as much as possible. Most hacking in public areas is opportunistic (yes, that phrase opportunity makes a thief is still valid), and if you make it a bit harder for the attacker, he will likely rather try and find another, easier victim instead.

