How much will an expiration of passwords improve security?
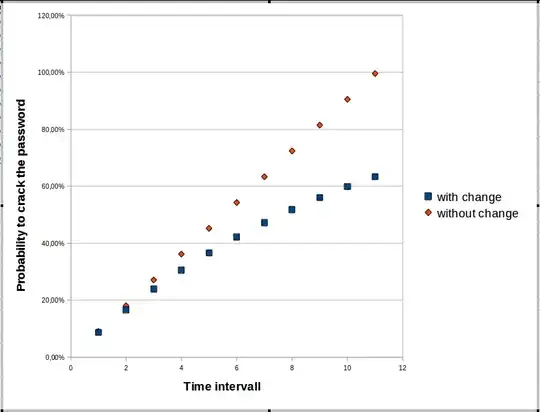 This image shows, for some scenarios, the relation between time and the probability, that a brute force attack on a type of password succeeded, depending on the regular change of the password.
The absolute timespan is of minor interest. How long it is - either there is not much difference, or the vulnerability is already pretty high.
This image shows, for some scenarios, the relation between time and the probability, that a brute force attack on a type of password succeeded, depending on the regular change of the password.
The absolute timespan is of minor interest. How long it is - either there is not much difference, or the vulnerability is already pretty high.
As mentioned from others before, there are different scenarios, where changing the password might help:
- a) User A tells a coworker B his password in a special situation. Later B is fired. He now might think about misusing the password of A (his own account is deleted, we assume), but it could need some time (losing a dispute against the company in court, for example) before starting his attack. Here, it is very useful, to change the password - but of course not from secret2010 to secret2011.
- b) Attacker has access to the shadow file, and is brute forcing with certain amount of CPU-power (or GPU).
In the case b), the policy to change the password, looks reasonable, but you do only profit, if the risk to be vulnerable is already really high. Let me explain it with numbers:
Assume an attacker might try 250 000 passwords per second.
Assume you say the password expires after 183 days, (about 6 months).
The password is generated from a-zA-Z0-9 which is 62 signs.
Assume the password is 8 signs long.
Check how probable is a breakin after 10 year, which is 20 change intervals.
I've written a program, to test different parameters; call the program with
java PasswordCrackProb 8 62 250000 s 183 20
len = 8
signs = 62
attacks per day = 21 600 000 000
change after days= 183
intervals = 20 days = 3660 years = 10
M = 218 340 105 584 896
attacks = 79 056 000 000 000
p(cracked) = 0,3620773 without change
p(cracked) = 0,3060774 with change
The result means, that it is cracked with 36% chance if the password wasn't changed, and with 31% if it was changed (but the attacker has a fresh shadow file). The difference is significant, and more so, if we take a longer time, 40 intervals, like 20 years:
p(cracked) = 0,7241546 without change
p(cracked) = 0,5184715 with change
but while 52% is much lower than 72%, 52% might not be acceptable.
But if we look at smaller intervals, the relative difference between changed and unchanged passwords gets smaller and smaller.
p(cracked) = 0,0905193 without change
p(cracked) = 0,0873006 with change
If you assume more CPU power or weaker passwords, the crack time gets smaller, of course, but the number of attacks per day is not very interesting. We have to assume: We can not enforce the user to change the password on a daily basis. So some days - maybe a week - is the minimum. And we don't need a maximum for longer than 20 years. Systems change, people change jobs. You cannot avoid to change the password after 20 years.
If the attacker has too much power, and brute forces the whole namespace in a single day, a weekly change won't help you much - he always wins. And if the attacker can only brute force 1% of the namespace (for a given password length) in 50 years, it doesn't help as well, to change the password - you will (nearly) always win.
Only in an intermediate, balanced scenario, the password change could make a difference, but do you really know, whether the bad guy needs 1, 10 or 100 years to brute force your password?
But keep in mind: If the attacker only once had access to your shadow file, which is now expired, the comparison from my program doesn't fit.
 This image shows, for some scenarios, the relation between time and the probability, that a brute force attack on a type of password succeeded, depending on the regular change of the password.
The absolute timespan is of minor interest. How long it is - either there is not much difference, or the vulnerability is already pretty high.
This image shows, for some scenarios, the relation between time and the probability, that a brute force attack on a type of password succeeded, depending on the regular change of the password.
The absolute timespan is of minor interest. How long it is - either there is not much difference, or the vulnerability is already pretty high.