Well i need to know is it possible to enter xss script through console of developer's tools(e.g. : firebug of firefox)? Is this a proper way ?
-
Could you expand on what you mean by, "...enter xss script through console..."? What type of attack are you afraid would happen here? – Abe Miessler Nov 07 '13 at 23:42
-
@Abe Miessler : Hi, basically this is my learning phase of security testing and i need to know from where all xss attacks can be done on our application. I have already tried with some xss scripts on my application and am successful in performing it. So i just needed to know if its also possible from console. – user2376425 Nov 08 '13 at 10:33
4 Answers
Of course its possible. Its literally a console that you can run and execute arbitrary JavaScript in.
As an example, here's me popping up an alert box on this very page: 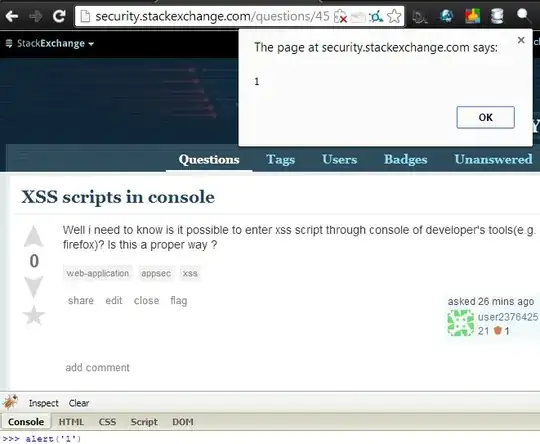
This is only dangerous if your end-user is stupid enough to run code in dev-tools that they don't understand.
Alternatively if there's an exploit available in the plugin your calling that may also be leveraged to exploit XSS attacks
- 11,426
- 17
- 77
- 111
-
-
@AbeMiessler there are several interpretations of this question and unfortunately its vague in asking. This -seems- like it answered OP's question. – NULLZ Nov 07 '13 at 23:34
-
I feel like you might not understand what XSS is. Lets take a look at the definition that OWASP has:
Cross-site scripting (XSS) attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user.
I would emphasize the last part of this definition: "...to a different end user."
In my mind, to qualify as a XSS attack you would need to submit a request to a website and have that site respond with the malicious content. The ways this can happen is typically broken down into two different methods:
Reflected XSS: Part of your URL is rendered on the page and the attack payload is part of your URL. You need to trick users into clicking your link to execute the attack.
Stored XSS: The XSS is stored on the server itself due to insecure programming. Then when a user visits the page with the XSS payload, the attack is called up from the server. The user just needs to visit the page, no link clicking required.
Based on the above I would say that XSS is not possible through the console. Rather you are just executing javascript of your choosing on your local browser. You would not be able to attack another user.
- 8,155
- 10
- 44
- 72
An attacker can use this to easily craft more complex payload make it return malicious urls, inject malicious JavaScript and things of the nature with the malicious link that will inject the attacker JavaScript.
-
Not exactly. An attacker needs to induce a victim the execute the script, and this is a wee bit more difficult. – Xander Jun 29 '21 at 00:40
You can change the maxlength attribute of an input by doing this.
first you look for the id of the input and you type this in the console
var inp = document.getElementById("id_name");
Then you change the maxlength attribute by typing this in the console
inp.setAttribute("maxlength","2000");
After doing that, you are able to type up to 2000 characters in the selected input.
This isn't an XSS attack by itself, but it if the victim depends on the maxlength attribute (without any server-side form validation) to protect there website then this will give the attacker the freedom to send as much code as they want to the server.
- 1
- 1
-
all this does is to overload the field when sending to the server. I cannot see how this is XSS or could lead to XSS. – schroeder Mar 05 '15 at 17:45
-
Well I tried this on a webpage of a game. Before you start the game it asks you for your name, and I found out that it allowed me to enter html code into the input. After the game finishes it shows you your name and the score. The only problem was that it only allowed me to enter 25 character. So I did this and I was able to enter an image tag with a grumpy cat photo. And when the game finishes it shows the image. – An_tho_ny Mar 05 '15 at 18:51
-
1ok, but then the XSS problem existed without you needing to do anything. – schroeder Mar 05 '15 at 21:00