To understand this, we must understand how crawlers find the email. While steering away from the technicals, the basic idea is this (today's algorithms are, of course, smarter than that):
- Find
@ in the page.
- Is there a dot within 255 characters after the
@?
- Grab what's behind the
@ until you reach a space or the beginning of the line.
- Grab the
. and what's behind it until you reach the @.
- Grab what's after the
. until your reach the end of the line or a space.
Now, an easy countermeasure would be to replace the @ with at and the . with dot. The most intuitive counter-countermeasure would be to teach the crawler that at is actually @. Well, it's not that simple. Take the following text:
We climbed into the attic and found a dotted piece of wood. Please email us: adnan at gmail dot com.
Now let's run our new crawler on it. First it will find the at in attic, then it will find the dot in dotted. The resulting email would be the@ticandfounda.ted, then it will find the second email adnan@gmail.com. Then spammers started teaching crawlers about finding certain domains, ignoring spaces, taking spaces into account, considering certain domain names, etc.
Then we started using images, spammers used OCR. We started using JavaScript tricks, inserting comments, URL-encide, etc. and always the spammers found a way to get around them. It's a race.
Having that said, the most basic techniques usually give good enough results (apparently, in some place in the world, that link is NSFW. Personally, I disagree), and the more obfuscate, the better results you get.
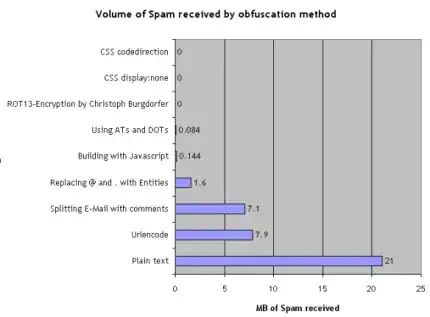
So, to directly answer your question: Is using 'dot' and 'at' in email addresses in public text still useful? Yes, I think so, at least to some degree. But this solution has been around long enough for us to assume that some crawlers have already found a way around it.
My advice? Either use some fancy advanced munger, or simply use images.
