Suppose the following scenario:
1- A web app (on WEBSERVER1) and its database (on DBMS1) having very sensible information deployed in the same physical server (lets said that for simplification). Users interact with the the web app under the umbrella of specials securities measures, these security measures take in consideration the fact that web app users are few persons and that those persons have an special network location respect where the DMBS1 and WEBSERVER1 are. I said this to sentence that some of the applied security measures (applied to protect the data in the DBMS1 and access to the WEBSERVER1) just can be applied to the users that meet this conditions, lets call this set of users USERS1.
2- Other users and applications (through API exposure) need access data (CRUD) in the DBMS1 too (lets call them USERS2), but we can't applied the same securities measures to USERS2 than we applied to USERS1 due theirs physical location, amount of users and control over them. Beside, is very important that authorization be enforced to USERS2, I mean, USERS2 just can access the data of the DBMS1 they were authorized to access.
One colleague suggest increase security having a different DBMS2 and a different WEBSERVER2 deployed, isolated from the main DBMS1 and WEBSERVER1, to allow USERS2 CRUD on data. As far I can see, this imply have a mechanism to synchronize data from one DMBS to another. Firewall and credentials could be set in a way that even DBMS2 server get compromised the intruder can't violate authorization policies and write data to DBMS1. To archive this must be a map between USERS2 authorization settings (specified in DBMS1) and the data replicated-syncronized between DBMS1 and DBMS2 and the process of data replication be initiate from server group of DBMS1, having them DMBS1 server the credentials to access DMBS2 while DBMS2 server don't know nothing of how to access DBMS1.
I think that the value this kind of architecture consist in having isolated-contained whatever exploitable security hole USERS2 could found in the deploy of the DBMS and the WEBSERVER2 which they are interacting with.
I just want note that USERS2 credentials protection and security measures compliance is outside the domain of the organization that management DMBS1.
My questions are:
Exist something written about this kind of architecture? What about tools/procedures to automatize the process of DMBS2 creations and modifications depending of authorization policies?
I would appreciate any help or orientation, critics about this architecture.
I'm including a diagram to support the explanation, arrow direction just matter regard of who initiate the communication... I know I know, the graphic is terrible, but I hope add some information.
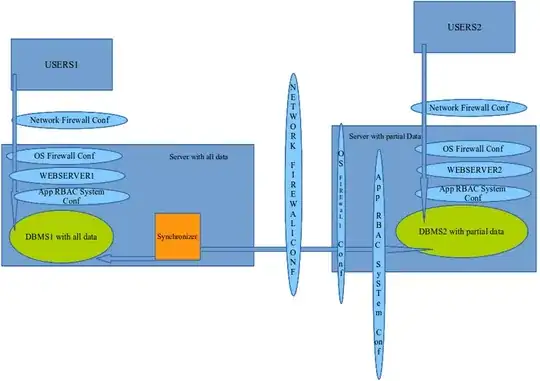
EDIT: Is evident the parallel of this DBMS-Web_Server architecture with the a DZM Dual firewall