Is anyone aware of an analysis of the TextSecure protocol?
https://whispersystems.org/blog/simplifying-otr-deniability/
https://github.com/WhisperSystems/TextSecure/wiki/Protocol
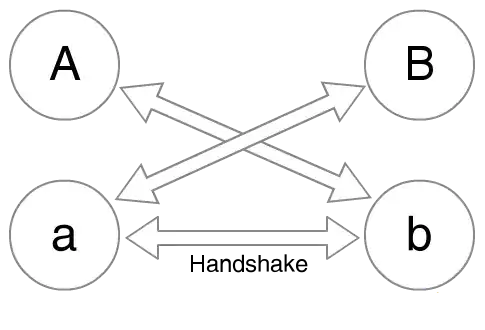
It is a simplification of the OTR protocol. Instead of signing the ephemeral key, it uses DH over an ephemeral key (a,b) and an identity (A,B) key.
The claimed advantages are: Reduced Algorithmic Complexity, Increased Forgability, Reduced Protocol Complexity, Maintained Forward Secrecy, and Smaller Payloads