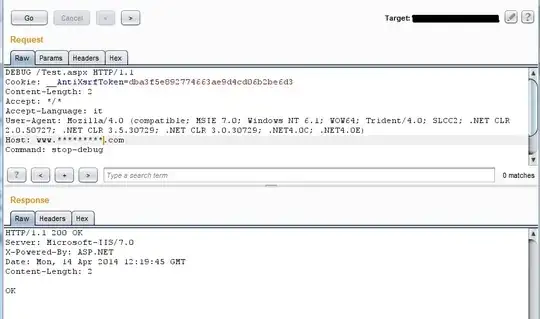
I know how to check this setting in code, and I know where to look in the web.config, but I can't seem to find information on how a vulnerability scanner like Qualys would detect this.
I've considered the following, but I have no way of knowing if my guesses are any good:
- Is there an http header that is sent from the web server when
Debug=true? - Is the scanner/software intentionally causing an error and detecting debug information reflected back to the client?
- Is the software looking for long-running requests (since debug mode effectively lengthens response times before a timeout occurs)?