Maybe you could help me with a small problem.
Would you recommend IPSec or TLS for a Server-to-Server-Connection? I need two or three arguments for reasoning a decision within my final paper, but sadly didn't find a criterion for an exclusion. The reflection of IPSec and TLS within my thesis is only a minor aspect, therefore, one or two main reasons for selecting TLS or IPSec would be enough. Do you think the possible compression within IPSec could be one of these main reasons?
More complete explanation of the scenario:
A user wants to login on a portal to make use of a service. The portal backend consists of the portal itself, a registration authority, user management, access control authority etc. Should I choose TLS or IPSec to secure those Backend connections? The delivered service does not have to be positionated within the backend, but it is reliable and is only connected with the portal. Here's a list with the connections I want to secure:
service (may be an external one) ---- portal
registration authority ---- user management
portal ---- user management
for a user-server-connection I've already made my decision, but the reasons I've used for this decision, doesn't work for a server-to-server-connection.
Thanks a lot in advance!
A picture of the scenario:
(red = problematic connection)
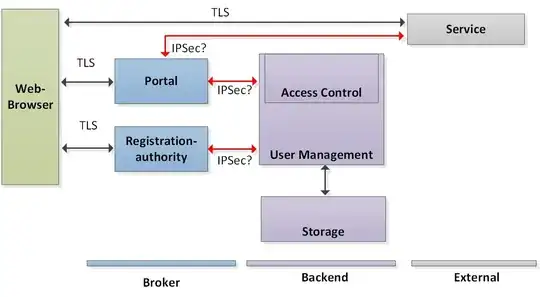
(in fact the model is by far larger, since I treat also other mechanisms like authentication, storage-mechanisms, storage access, access control, software-architecture, including possible technologies and so on. Therefore, securing the connections is only a partial aspect)