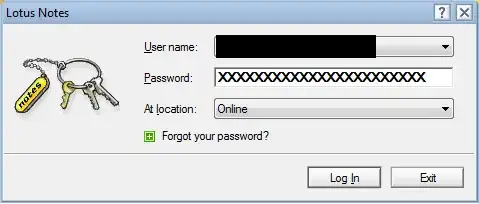
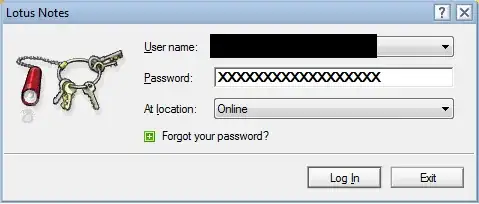
There is some information on this defunct page. Apparently, the idea that the "moving picture" is there to distract shoulder surfers is widespread, and wrong. That's not how this picture works; what it does is actually worse, although it proceeds from good intentions.
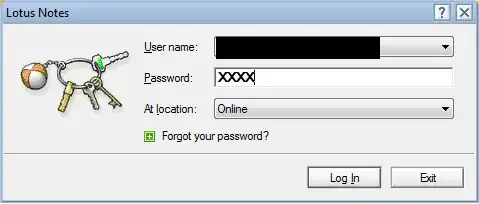
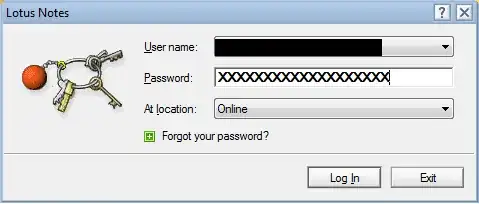
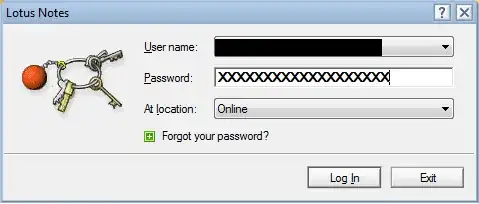
When you type the password letters, Lotus employs a "fairly complicated" but deterministic algorithm to map the password as entered to a picture; this basically is a hash function with a very small output size (the output is a "value" in the set of possible pictures). It is possible that the said hash function includes some server-specific secret, but it won't matter much. The real point is that, as you observe, when you enter your password you always end up with the same picture for a given password. The good intention is to achieve the two following properties:
Give an early visual warning as to whether the password was entered correctly or not; the user will soon learn the sequence of pictures for his own password, and thus if a picture changes, then the user knows that he typed the wrong key at that point (or possible a few characters before).
An attacker who tries to mimic this login popup and make the user type his password in a fake popup would supposedly find it "difficult" to recompute the pictures and display them correctly.
The second reason is pure baloney, when you think about it: the "complicated algorithm" cannot be kept secret (especially if the fake popup is actually a man-in-the-middle attack and the true popup is used under the covers to get the actual pictures), and making pictures which move on the screen is really easy: that's what 99.9% of the Web is about.
The first reason, however, includes the seeds of destruction: this leaks information on the password. The pictures are on the screen and very visible; quite prominent, even. The "shoulder surfer" can see them from afar. And he can use them to prune out potential passwords. Indeed, if there are four possible pictures, then this leaks 2 bits per character: for an 8-character password, which would have, realistically, about 30 bits of entropy, this is then reduced to a meagre 14 bits.
Indeed, this feature is analogous to a system which would write on the screen, in big letters, and for each password character: "this character is a digit" / "this character is an uppercase letter between A and M" / ...
Therefore, this "picture" system is downright dangerous and should be banned.
As for the password length, the number of characters is very easy to get for the attacker, because each key stroke is highly audible. The shoulder surfer just needs to be within earshot of the victim, and could easily record the sequence with his smartphone to listen it later on, suitable slowed down, and thus obtain the password length. Under these conditions, hiding the length from the user himself is pointless.