TLDR. It can be secure if you configure it properly and use good long passwords.
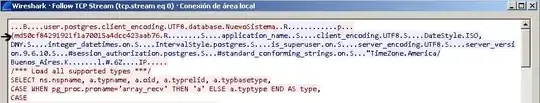
1. In postgres the md5 auth-method means client-side hashing (discussions: 1, 2), which makes hashes password equivalent. A hash in the db is compared to a hash received from a client. An attacker can use any hash from stolen pg_shadow table directly, without even spending time to crack the md5.
It's much safer to assume the hashes will be stolen eventually and to avoid client-side hashing.
You can actually just take a look at the code, it's quite simple: https://github.com/postgres/postgres/blob/master/src/backend/libpq/crypt.c#L141 <— direct link to this line:
if (strcmp(crypt_client_pass, crypt_pwd) == 0)
See what happens when the port->hba->auth_method == uaMD5. Yes, one can't intercept a hash clear-text, it's again salted and hashed. But when stolen by any other attack, it can be used directly without cracking.
2. Unsurprisingly, you can use server-side md5 hashing with postgres by using the password auth-method and create user whatever with encrypted password.
These methods operate similarly except for the way that the password
is sent across the connection, namely MD5-hashed and clear-text
respectively.
Use SSL to protect the clear-text password. You probably should know the way its hash is stored — the salt is reused:
/* Encrypt user-supplied password to match stored MD5 */
if (!pg_md5_encrypt(client_pass, // const char *passwd
port->user_name, // const char *salt
strlen(port->user_name),
crypt_client_pass)) // char *buf
One could even create random generated throwaway usernames to use them as salt, but I'm not sure if it's a good idea, this is error prone.
While the general recommendation is to migrate from md5, it's still not broken for password hashing. Relevant question: Why do people still use/recommend MD5 if it is cracked since 1996?
Don't use short passwords. Long, high-quality random passwords are still safe.
For a quick estimation, these (unfortunately, quite old) links have some numbers:
http://blog.codinghorror.com/speed-hashing/
https://security.stackexchange.com/a/33684/41687
Update: thanks to RhodiumToad from #postgresql channel on irc.freenode.net for clarifying that md5 is still not broken for password hashing, good long passwords will save the day.