Today I changed the SSL certificate that 3,000+ Outlook clients are using. In doing this I changed the certificate to an "older" one that had the same subject name, expiration and everything else. Only the thumbprint and one SAN name changed. Once reports came in of an issue, I reverted the change. (1 hour)
It seems that in doing this several deployed instances of Outlook hung, and despite my 15 years of working with Outlook in a support capacity, I couldn't salvage the profile and had to recreate it. (I don't want to repeat this process for the remaining 20+ profiles)
I can only assume a SSL cache exists in Windows, Outlook, or in it's IE dependency.
This brings me to my question:
What SSL data exists in the IE SSL state button? Is this a cache of web HTTP data, or certificate data?
Is there a per application SSL cache and/or a global one? (e.g. schannel, etc)
How do I edit or manage this cache?
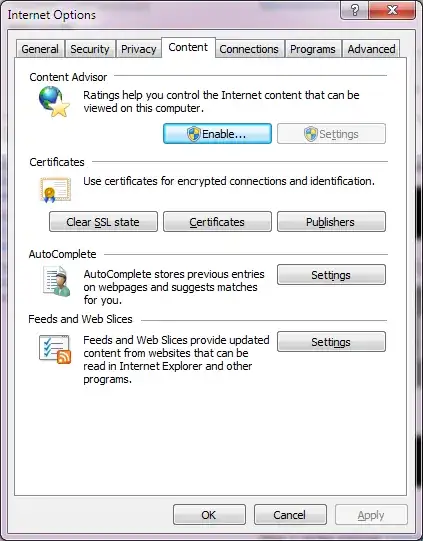
Here is a picture of the SSL editor in IE (see "Clear SSL State")
Update:
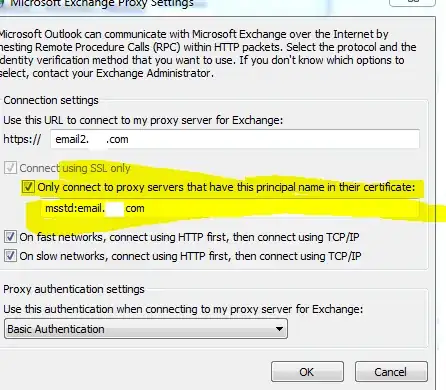
Even though the certificate is properly formed, unchecking the following text box in Outlook configuration appears to correct the issue