I'm using NMAP for Network scan ;
The output does not contain the full traceroute details. Can I view all intermediate routers/hosts using the NMAP GUI?
A simple VPN connection IP traceroute...
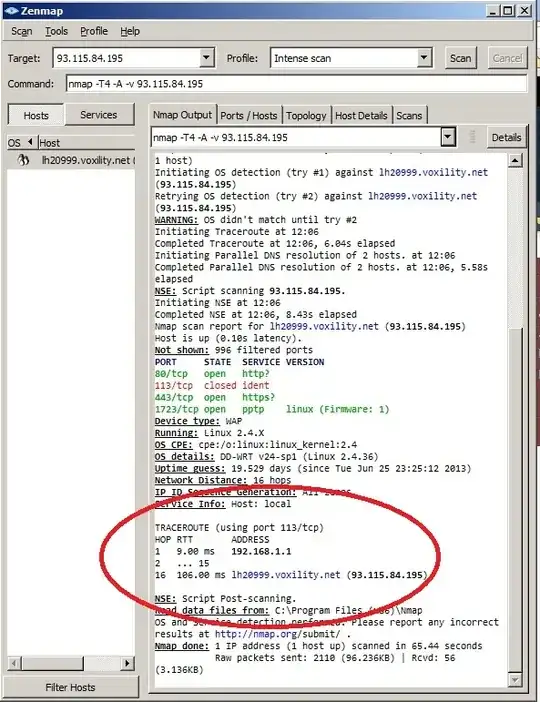
Thanks your answers...
I'm using NMAP for Network scan ;
The output does not contain the full traceroute details. Can I view all intermediate routers/hosts using the NMAP GUI?
A simple VPN connection IP traceroute...

Thanks your answers...
Try with this command
nmap -sn --traceroute <remote_ip>
And lookup these:
https://serverfault.com/questions/432017/whats-going-on-with-traceroute
https://svn.nmap.org/nmap/zenmap/share/zenmap/config/scan_profile.usp
This output simply means that none of the intermediate hops returned an ICMP TTL-expired message, so Nmap couldn't show any details. This is most likely because it used port 113, which historically is often blocked by ISPs because of security problems with the Ident protocol. The closed-port response probably did not come from your intended target, so it wouldn't be a good port to use for traceroute anyway.
To get usable results, you could try a few different things:
In the next release of Nmap, the scoring function that decides which port is used for timing and traceroute probes will prefer ports other than the commonly-spoofed ports of 25, 113, 135, 139, and 445. It would not help in your case, however, since closed ports are more strongly preferred than open ones, and 113 is the only closed port in the scan.