So I'm at place A, see this sign:
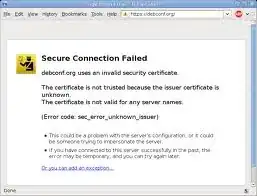
and I'm writing the fingerprints to a piece of paper (this website is just an example):

Ok. Then, I go to place B (other country, etc.) then I check this site. The sign (for the self-signed cert) shows up again, OK. But: I get my paper out, and check the fingerprint of the site. It's the same.
QUESTION: With checking the fingerprint of the website, could I be 100% sure that:
- I'm visiting the same site (server) on the two places (so no one can produce this fingerprint on other server?, MiTM?)
- I'm secure because the content of the HTTPS connection cannot be sniffed.
p.s.: I'm using private browsing with Firefox on my notebook. The server side is mine too, I generated the self-signed certs. The notebook side were rebooted in the meantime, so I have to click again that: "I accept the risk, proceed anyway"