I am filtering all images that attached to any content of my blog:
- Check for file extension.
- Check content type using
$finfo = finfo_open(FILEINFO_MIME_TYPE); - I also save the image temporary on my server and check the size using
getimagesize()then I delete it if the function not returned false.
But after these checks, I will not re-check the image.
What happened to me
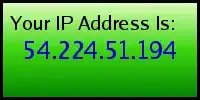
On one user profile I can see my IP address on the image each time I visit the user profile. This is an example I attached to this post:
Now, I can conclude that allowing user to attach any image will be dangerous because of this cloaking file attack that can generate dynamic image on each request.
Is there any mechanism to prevent this?
or should I remove all attached images from user profile and saving each image on my server