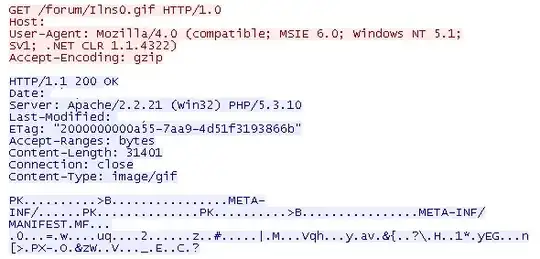
How is it possible to use an incorrect type and still get the file loaded by the user?
If it were the browser loading it, it would indeed get handled as a GIF, and fail, in general. (There are content-sniffing problems in web browsers, but not ones that would trigger here.)
However, when you instantiate an applet with the <applet src>/<object data> attribute pointing at it, the Java plug-in loads the address as an applet class/jar, regardless of the Content-Type you serve it with.
(That's not a good behaviour, but it's a symptom of the continuing MIME malaise - browsers/plug-ins don't want to be strict about requiring correct media types because so many servers are set up wrong, but UAs being permissive about media types means that lazy admins don't have to set up their servers right...)
This is especially pernicious given that Java's bizarro version of the Same Origin Policy operates primarily on the source of the class/jar rather than the containing document page - if you can put an applet file on someone's server you can, to some degree, cross-site-script into it. However it doesn't look like the attack made any use of this - exploits work regardless of origin.
It's often difficult to spot this because it is (/was) possible to create a polyglot file that is a valid GIF and JAR at the same time ("GIFAR"). However, again, this hasn't been done here. The attacker can choose any filename/type they like for an applet, and apparently they thought a GIF would be less conspicuous than a JAR.