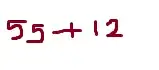Security is about balancing costs and risks, nothing is impossible to beat, specially not typical CAPTCHA implementations, but they do add something no other system seems to offer.
I've been reading around about these CAPTCHAs for a while and possible alternatives... (so please don't refer me to other sites/answers unless they truly answer the following question).
I have no experience whatsoever, so for me it is hard to estimate the costs and risks associated with this decision: should I employ CAPTCHAs (I'm thinking of JCaptcha or reCaptcha), or are a combination of other techniques enough?
I have a registration form to be filled, but I don't want my user table to be filled with trash. Honeypot field is easy to implement, but oh so easy to circumvent, simple security check (what color is the sky?) works well against automated attack, but any 15 year old can build a simple targeted attack that wrecks my user table...javascript to check time taken to fill the form is insecure and with a simple post to my server broken. Basically, I haven't found anything that works vs a slightly smart targeted attack except a typical CAPTCHA so I don't get trolled... So the real question is, am I at a significant risk of getting trolled with a targeted attack so I'd rather lose 10% of my users to these CAPTCHAs or is there an alternative that doesn't tax so much the user?
EDIT: Thank you so much for your answers, it certainly has helped me clarify ideas, specially the link to OWASP about avoiding brute-force attacks (got my +1, but I did not accept it since it didn't feel like a solution, but it does help find one. If you think I should accept it because I find it the best answer so far, please comment saying so since I may be misinterpreting the workings of the site).
On the other hand Asirra is quite fun and easy, and a lot better than traditional CAPTCHAs, I certainly would recommend it over other services. The puzzle is a lot more fun, and even if you fail, you would only fail once... pity:
Asirra is still in beta-testing; the service and its API may both be unstable.
Final Edit: Just in case it is found useful, here are the steps I've taken to ensure users are not bothered by CAPTCHAs but I feel safe from bots.
- honeypot field (so easy to implement it cost me nothing though I don't feel very secure with it.)
- e-mail verification link (or OAuth access) since it was always on my plans to add it. only validated users are migrated to my user table, the rest stay as registered.
- time check: server time-stamp with signature loaded through ajax, user needs to take at least 5 seconds to fill the form before sending (the password) or it is discarded.
- confirmation page (with server signed token to ensure the request has passed through the server first) after registration that warns the user that confirmation e-mail is required and has a button to send the confirmation e-mail. (In which case the data is also registered on the DB)
This will not stop a very dedicated attacker but I hope they will not want to spend hour and hours tuning his attack to gain nothing, just bothering me.